Last week, Tim Parisi, the Director of Incident Response for CrowdStrike’s world-class IR services team, published a blog detailing “multiple investigations into an intrusion campaign targeting telecommunications and business process outsourcing (BPO) companies.” In this piece, Parisi explored several techniques adversaries employed to establish and maintain access while evading detection. He also shared guidance for organizations looking to protect themselves against this ongoing campaign.
Our team at Obsidian Security was particularly excited by our inclusion in the team’s investigation and subsequent blog post, a recent honor only adding to our important partnership with CrowdStrike.
There’s no question that the CrowdStrike team’s analysis of the incident and guidance are incredibly thorough and worth the read. Given our unique perspective as a SaaS security focused company, we thought it worth diving even deeper into some of the guidance shared in the CrowdStrike blog and expanding on the Obsidian capabilities that make rapid SaaS incident response possible.
What happened, and how did Obsidian help?
Initial Access & Attack Persistence
According to Crowdstrike, over the past few months, there have been “persistent and brazen” attacks on telecommunications and BPO companies in attempts to gain access to mobile carrier networks.
To establish initial access to SaaS apps, attackers employed social engineering, impersonating IT staff over different communication channels. Victims were instructed to either navigate to a website that would capture their credentials or install one of many different remote management tools, granting the attacker persistence in the environment.
Obsidian activity monitoring and threat detection capabilities were critical in uncovering and addressing the presence of threats.
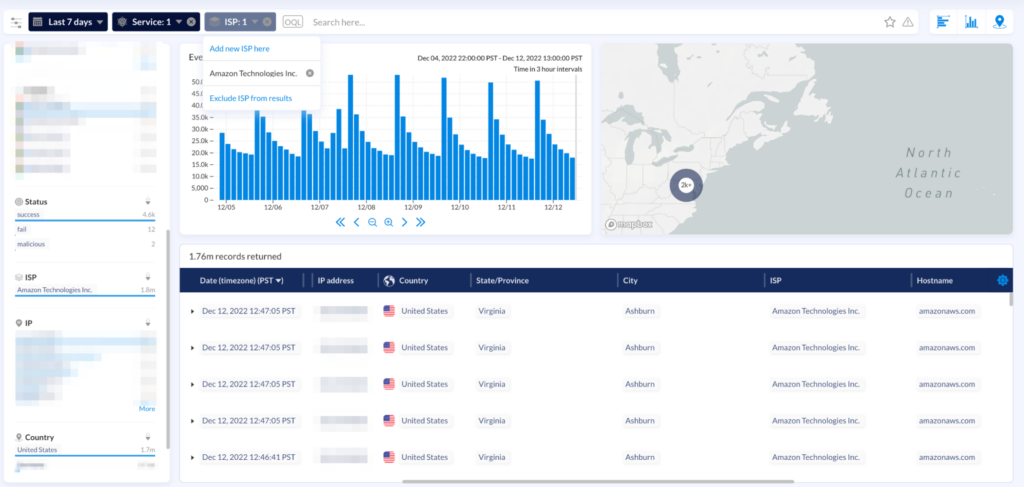
Obsidian lets users drill down to traffic of interest using filters, and pivot points to look up the reputation of an IP address and check a user’s geo history for curated data analysis.
This enables customers to identify potential impacted user accounts from IPs, ISPs, ASNs, or proxies in question and conduct further investigation.
In addition to looking into the past, Obsidian enables customers to create custom detections based on IPs, ISPs, ASNs, proxies and a host of other criteria, which utilize built-in pivot points to identify activities and then receive custom alerts to notify them of future activity.
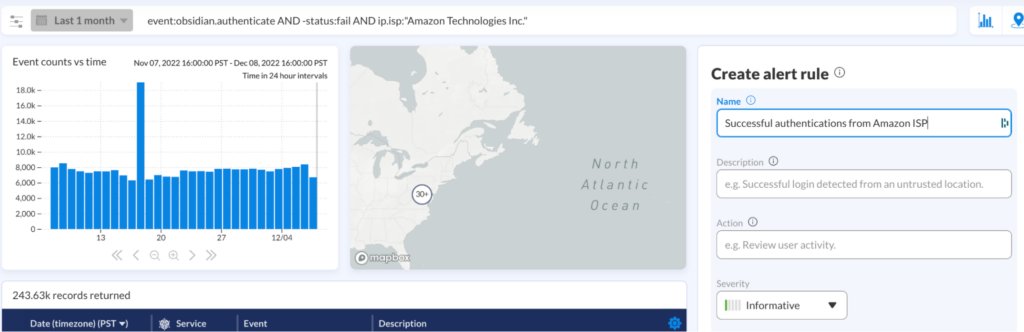
The CrowdStrike IR team used these activity search and custom detection capabilities to uncover malicious activity originating from specific ISPs from which adversaries were operating—and then promptly implement restrictions.
Although Obsidian comes ready out of the box with a wealth of threat detections informed by our team’s expertise, the platform offers tremendous flexibility to search, hunt and alert on more specific parameters unique to your organization or, in this case, a certain intrusion campaign.
Gaming Multi-factor Authentication
Although a number of users had enabled MFA on their accounts, attackers were able to bypass these protective measures in several different ways. One technique employed was MFA fatigue, where a user is literally flooded with requests to approve a sign-on until they accept one. (This very attack is covered in an article by Obsidian’s Head of Information Security, Alfredo Hickman, which explains exactly why MFA isn’t bulletproof.). Through the Obsidian activity component, the timeline of suspicious login involving MFA fatigue can be spotted with clarity.
After successful initial access, threat actors may register a new MFA factor to persist. Obsidian activity component is able to help IR analysis to locate when an MFA factor is registered where, and also provides statistics on how frequent a factor is used to establish a baseline.
The number of recent, newsworthy breaches that involved MFA circumvention has emphasized the importance of configuring a strong MFA implementation and supporting it with robust activity monitoring capabilities. Obsidian’s powerful threat capabilities and industry-first token compromise detections help teams promptly identify and address attacks that bypass MFA measures in any number of ways.
Sensitive Data Exfiltration
CrowdStrike explains that once attackers had breached critical SaaS platforms like Microsoft 365, Google Workspace, SharePoint, and OneDrive, they almost immediately began searching for and exfiltrating sensitive internal documents in bulk. This helped them understand internal processes, determine privileged users, and work towards their apparent end goal of accessing mobile carrier networks to perform SIM swaps.
Obsidian’s integration with the CrowdStrike Falcon platform provides security teams with seamless visibility into activity stretching across their entire “last mile” from endpoints to SaaS.
This powerful connection enables even deeper correlation of telemetry from both platforms, so incident responders can precisely monitor threats that move from devices to the cloud and laterally between interconnected applications.
How can Obsidian help me implement protective measures?
The CrowdStrike blog concludes with a number of best practices for security teams looking to protect their organizations from this and various other threat campaigns. Every piece of advice is sound; we thought it would be helpful to unpack a few of these recommendations and explain how to implement them with Obsidian.
Ensure most users are routed via SSO
Often Obsidian finds that users are still logging in locally because they have maintained inappropriate local access to SaaS applications. The general user population should always be only managed via an IDP. Local access should be restricted to legitimate users such as administrators and service accounts.
Enforce MFA and configure it properly
Secondly, ensure that MFA is deployed for all accounts in your organization both for your SSO and local access. Make sure all of your IDP policies enforce MFA.
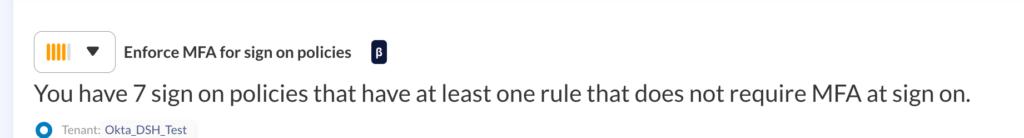
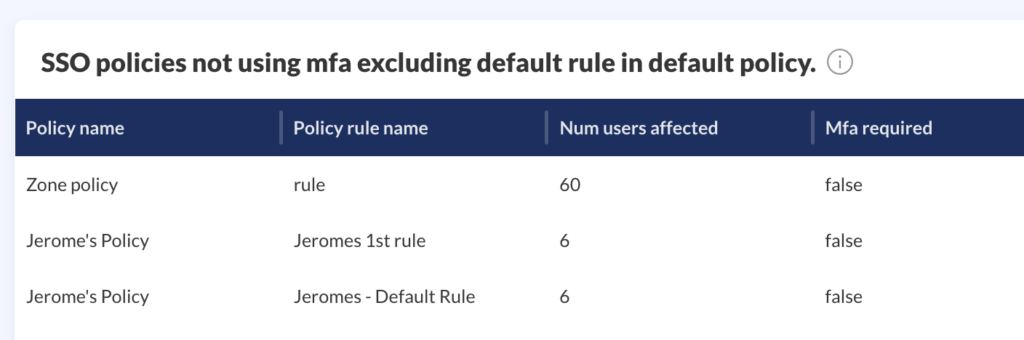
Then, consider the way you’re implementing MFA and the varying security levels of different factors—for example, hardware security keys are more strongly recommended over SMS. Explore policies that throttle bulk actions to deter fatigue attacks, and implement limitations and review around the enrollment of new MFA devices to minimize opportunities for attacker persistence.
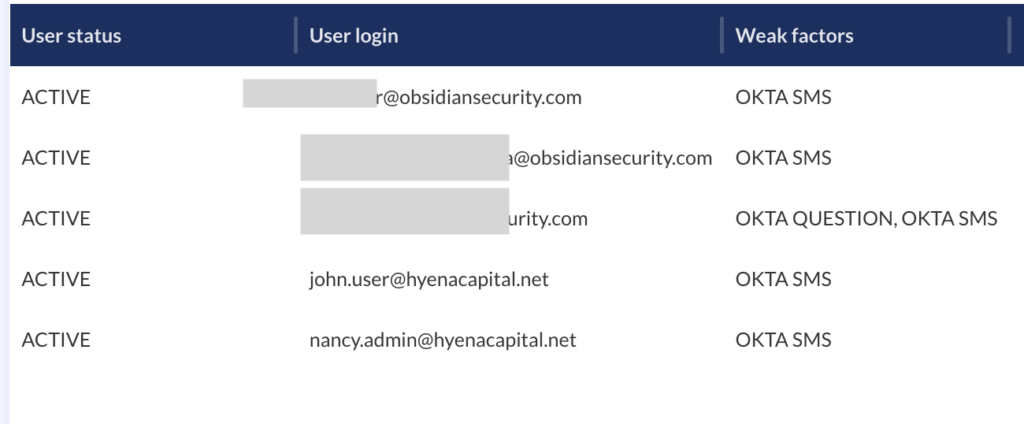
Obsidian continuously monitors your SaaS configurations to uncover misconfigurations in your authentication methods and help your team proactively address these gaps. These can include administrator or privileged accounts without MFA, the presence of weak MFA methods, and limitations around failed login attempts. Every misconfiguration is accompanied by useful context around affected services, impacted users, and the necessary steps for remediation.
Monitor and manage privileged user accounts
In their security guidance, Parisi and the CrowdStrike IR team recommend adherence to the principle of least privilege, a concept that limits users’ access rights to only what is required to fulfill their duties. While sound advice, manual implementation can feel almost impossible across dozens of SaaS applications and in environments with hundreds or thousands of different users.
Obsidian gives teams a scalable and straightforward approach to managing privileges across SaaS. By analyzing activity data and comparing users to their peers, Obsidian recognizes when privileges aren’t being used or are unnecessarily generous for a specific role. With this context, security teams can make appropriate reductions with full confidence that they aren’t unknowingly impacting or interrupting business operations.
Be cognizant of security control bypass attempts
If proactive security measures like MFA are equivalent to a reinforced front door to your home, threat monitoring is like the security system within the four walls. As sophisticated attackers find new ways to bypass preventative solutions, it’s important to complement initial lines of defense with tooling that helps you understand exactly what your users are doing and when this activity is putting your organization at risk. For instance, you can build a custom alert for MFA registration events if you don’t expect them to happen frequently in your organization.
Obsidian’s robust threat detection capabilities are so critical to incident response teams looking to identify and investigate compromises, insider threats, and SaaS integration abuses. You can also visualize user activity within applications and laterally across multiple services to get a precise timeline of events. Powerful machine learning models continuously baseline user behavior to spot the earliest unusual signs of a threat and help teams respond rapidly and minimize impact.
We at Obsidian are working alongside CrowdStrike with a commitment to supporting businesses across industries that are vulnerable to attacks. To learn more about Obsidian’s partnership with CrowdStrike and how we can help organizations better protect against threats, visit this page. You can also find more detail on the integration on this solution brief.