While the goals of various adversary groups may not change drastically over time, their tactics, techniques, and procedures (TTPs) will. Effective techniques for initial access, post-authentication activity, and dwell time within a target tenant are an attacker’s bread and butter. The cliche of “emerging identity threats” is actually a blurred line between simple IOCs and cutting-edge techniques.
In this blog post, we explore the unique aspects of residential proxies in identity phishing attacks. We’ll go over some IOCs you can check in your own environment and cover some strategies for detecting current and new trends in these attacks.
Our Unique Observations on Emerging Identity Threats
In recent weeks, Obsidian observed a set of unique characteristics across several targeted attacks, distinguishing them from others of a similar kind:
1. Residential Proxy Usage
Phishing kits and services are taking advantage of proxy networks that utilize a variety of residential IPs. To evade detection and get past conditional access policies, attackers can appear in the same city as a victim while also coming from a residential ISP such as Comcast, Cox, T-Mobile, Verizon, etc. This gives attackers an advantage as opposed to coming from IP space associated with private VPNs or hosting infrastructure which is easier for defenders to identify. As you can imagine, this muddies the waters when performing detection engineering, security operations, and incident response.
2. "Zscaler Inc." ISP Minted a Malicious Session
Residential proxy networks involve both willing and unwilling parties leasing their bandwidth and IP addresses to other users. These networks are built, deployed, and utilized in various ways, as extensively detailed in a blog post by Sekoia.
In one incident, although the victim organization was not a paying customer of Zscaler, an ISP associated with Zscaler appeared in a compromised login sequence. These logins matched others that were confirmed as true positives, all of which passed through residential proxy IPs.
To our knowledge, Zscaler can operate in a VPN mode via Zscaler Client Connector, potentially routing all machine traffic through its infrastructure. This includes traffic from a residential proxy agent or through a compromised host.
During our testing, residential proxy agents successfully identified residential IPs and routed traffic exclusively through these IPs. However, our testing was not exhaustive, so we cannot definitively exclude the possibility that the Zscaler IP originated from a voluntary proxy agent.
Whether from a residential proxy agent or a compromised host, the mixing of residential IPs with security gateway IPs can significantly complicate security measures for obvious reasons.
3. Outdated User Agent
In addition to the use of residential proxies, the attackers used an outdated Chrome user agent released in 2019. While detecting phishing through residential proxies poses a challenge, this simple IOC has a very high success rate in identifying these attacks.
4. Consistencies in Phishing Login Sequences Across Multiple Tenants:
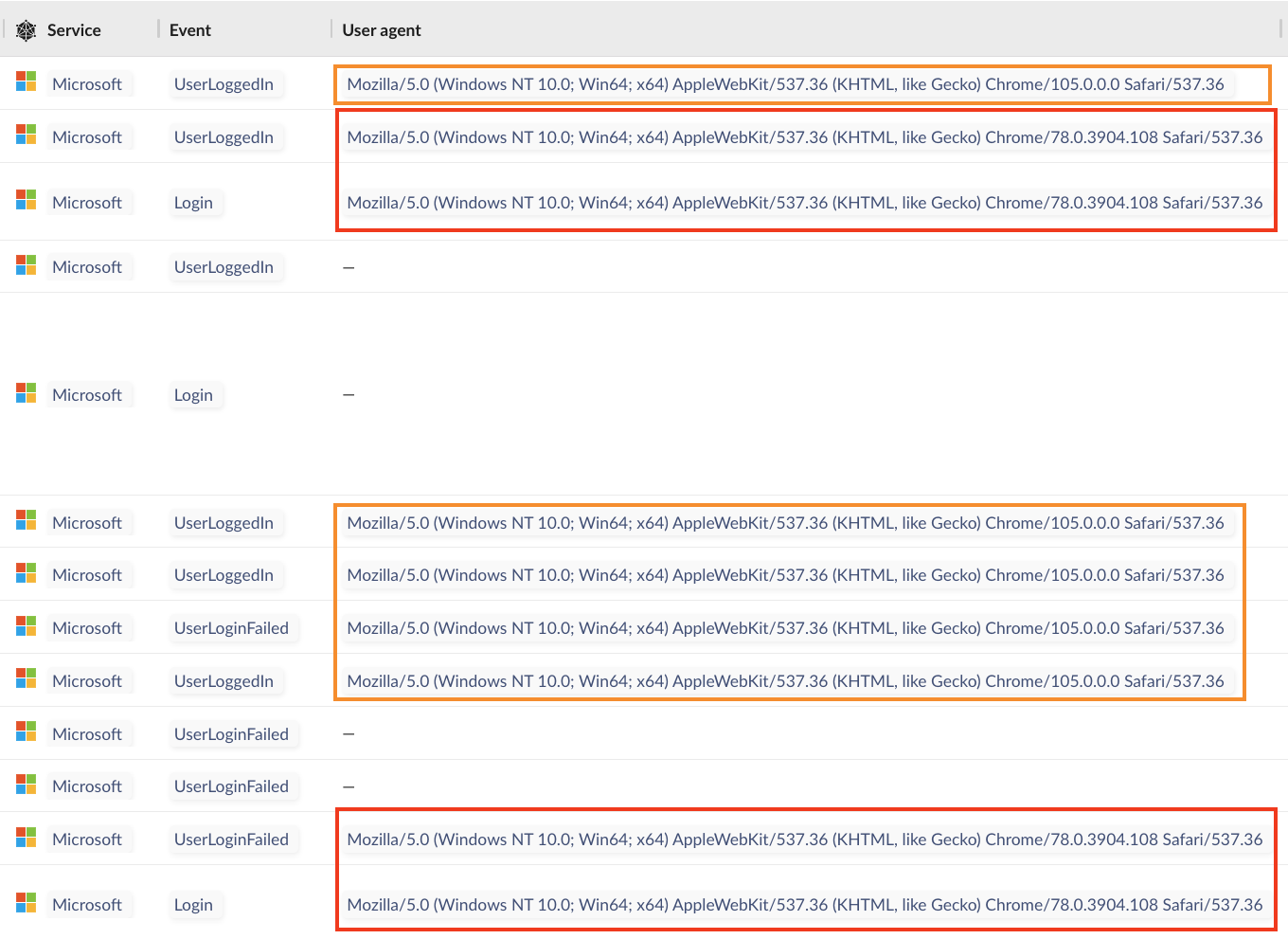
When investigating the outdated user agent string across our tenants we noticed a consistent sequence in the stream of login events during the phishing attempt. The below screenshot shows alternating jumps in Chrome versions 78 and 105. These patterns were consistent across multiple attacks when the Chrome 78 user agent string initiated the login sequence.
OAuth Integrations Utilizing the EWS.AccessAsUser.All Scope.
Obsidian possesses insights into thousands of unique integrations that organizations use to operate their businesses. Among these, two commonly observed applications are “eM Client” and “PERFECTDATA SOFTWARE”. The functionality offered by these applications, combined with their broad scope, makes them appealing tools for attackers. Nearly every instance of their usage coincides with malicious activity.
This type of tactic is not brand new and reports of their usage by bad actors began in 2023 in a blog post published by Darktrace and another blog post published by an independent researcher. While these IOCs are simple and slightly old, they can often be an effective signal that does not rely on detecting the more advanced TTPs.
Utilizing Identity Triage
Thanks to residential proxies, our once reliable geo anomaly detections will be less effective in detecting adversary activity. Geo anomaly detections are only one aspect of the kill chain; solely relying on these will not suffice. We highlighted this topic in a previous blog post, Rethinking Identity Threat Detection: Don’t Rely on IP Geolocation.
Moving forward, we must adopt an identity-centric approach that prioritizes evaluating the overall activity of a user rather than solely reacting to individual alerts. By adopting this method, we can better spot suspicious account behaviors, avoiding getting bogged down in the minutiae and edge cases that a single alert might present.
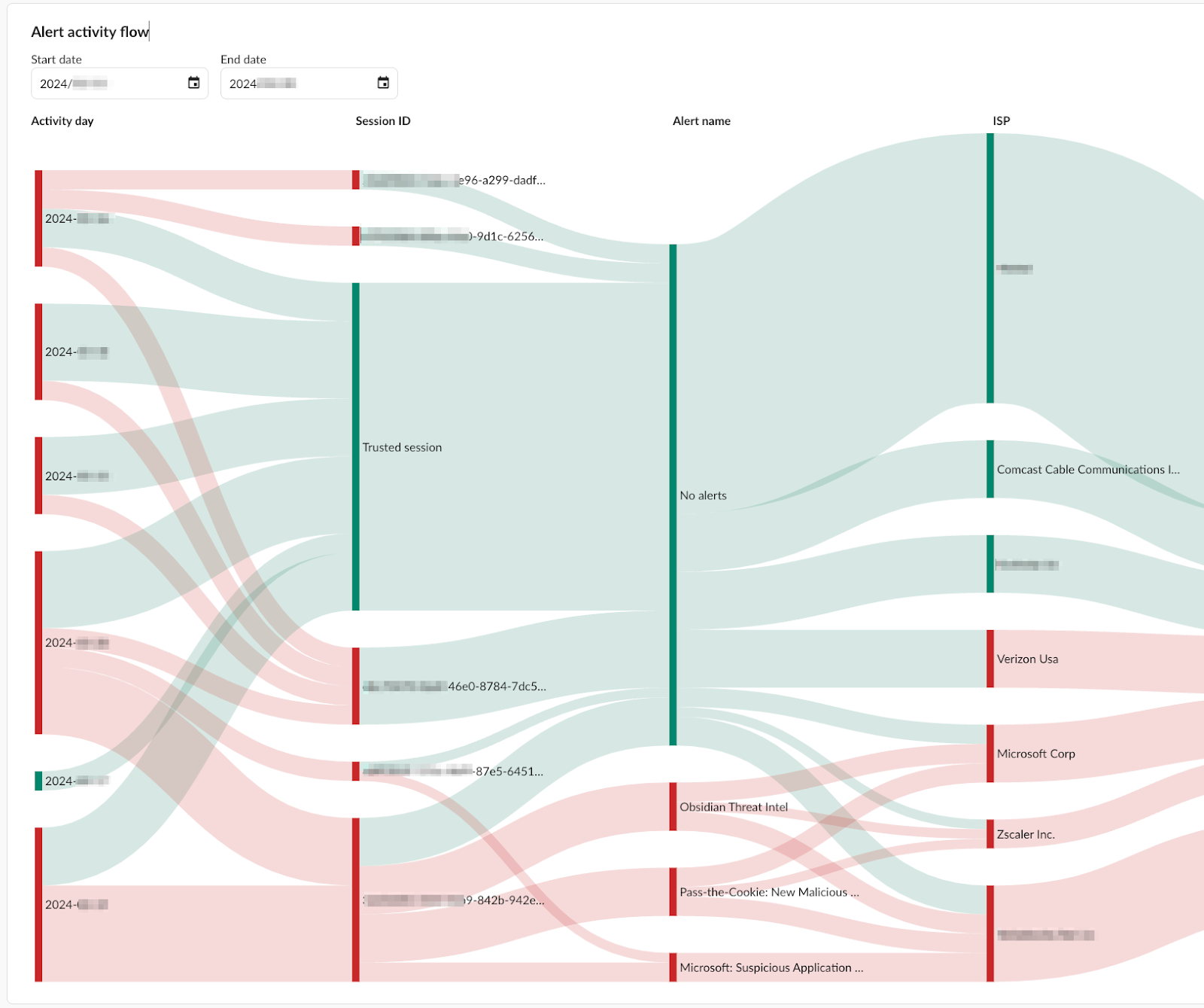
The below screenshot is an example of how using an identity-centric triage method helps understand a compromise without getting bogged down in the complexities of emerging TTPs. Paying close attention to suspicious activity as it contrasts with the baseline behavior of an identity will lead to a smoother process in successfully identifying identity compromise.
Takeaways
- Check your tenant for the below IOCs. Activity from these indicators should be carefully examined.
- “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36.”
- “eM Client”
- “PERFECTDATA SOFTWARE”
- Adopt an identity-based triage strategy. Group all of the alert telemetry from your security products by individual users. If your phishing solution misses an attack, tooling from your identity threat products like Obsidian will be able to fill in the gaps.
- Adapt your detection and incident response methodologies to account for the rise in malicious residential proxy usage. Do not solely rely on geo anomalies when writing detections. During an account investigation, don’t simply disregard activity just because it’s originating from a location you typically associate with benign behavior. These locations are now being used by attackers for exactly these purposes.




