Organizations around the world have moved their critical business processes and sensitive data into SaaS applications. While SaaS adoption is delivering enormous business value, it has outpaced the ability of security teams to stay updated on new applications to monitor and secure them. Security teams, often understaffed and overworked, have to figure out how to safely enable the use of SaaS without slowing down the business.

Even experienced security teams that understand risks and threats grapple with operational challenges when it comes to actually doing it 24/7. Many of these challenges are unique to SaaS. For example, each application maintains authorization and entitlement management inside the platform. Entitlements are buried deep in application specific formats, creating visibility silos. Every application implements its unique model of access, privileges and roles that determine what users can access and do in the applications.
Applications also vary a lot in terms of security configurations and controls they expose to customers. Office 365 and Salesforce offer a rich set of controls and hundreds of configurations, while Slack has just a few. Customers are responsible for configuring these applications appropriately and consistently according to security best practices, and ensuring that configurations don’t drift. This is easier said than done. Even a seemingly small misconfiguration can leave users and data exposed and unprotected. Security teams are often out of the loop when it comes to configuring and managing SaaS apps.
Take 1: “Roll Up Your Sleeves” Approach
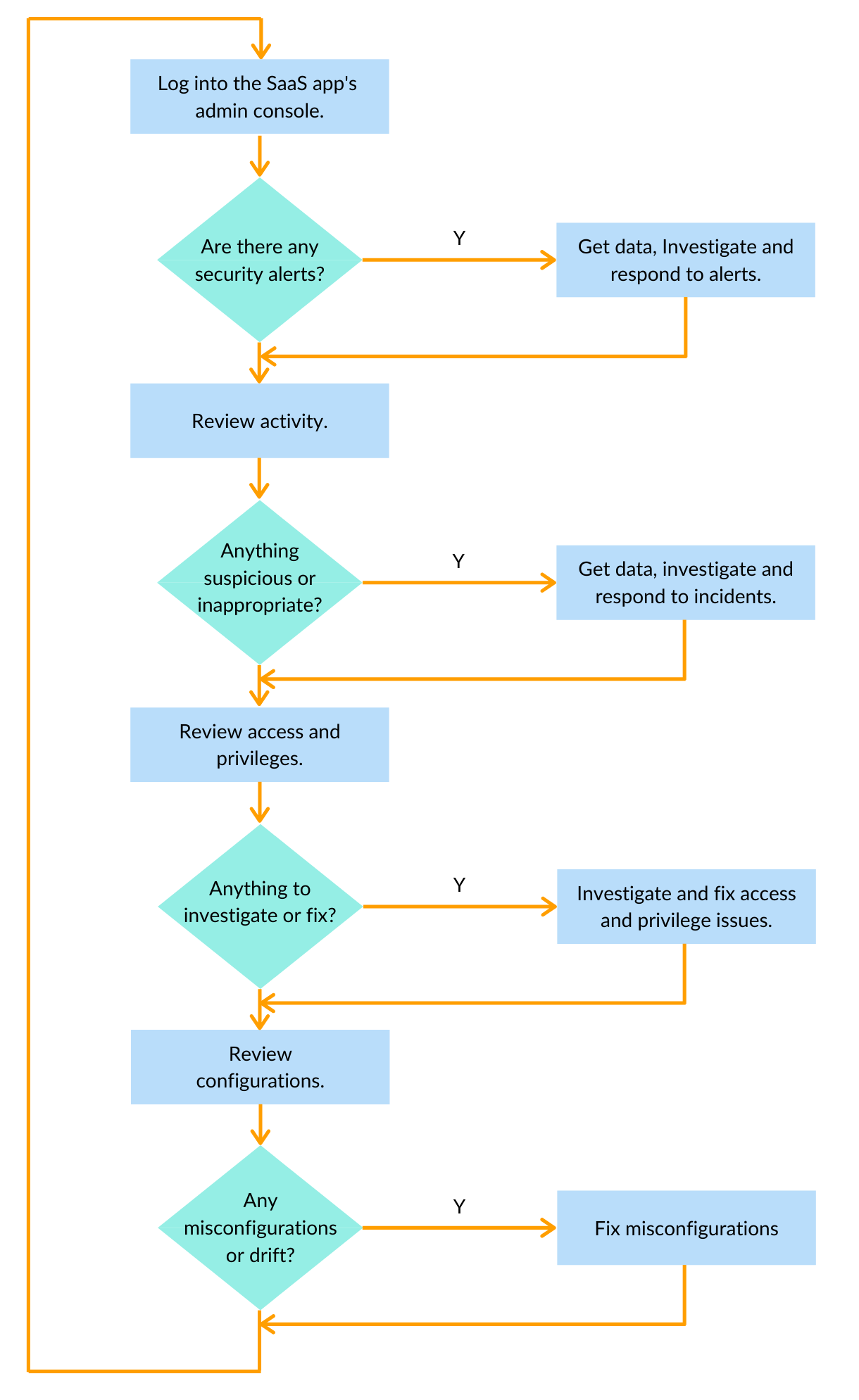
Security teams often start tackling SaaS security manually. An administrator inspects and monitors users, privileges, activities, configurations, and application-generated alerts regularly for each of the apps that she is securing by following these steps:
- Log into a SaaS application’s admin console.
- Check if there are any alerts generated by the SaaS application that need investigating. Applications are at different levels of sophistication in what security risks and threats they can detect and alert on.
- Navigate to the activity log and see if there is anything suspicious or inappropriate. Has someone shared a file or data store broadly? Was there a large number of unsuccessful login attempts from an unfamiliar location? Did an admin login without using MFA? This data is presented in different places and in different formats in each app.
- Navigate to where the data about users and privileges is located. Check who has privileged access, and make sure that there are no unexpected privilege assignments (e.g., backdoor accounts and rogue privilege elevation). Navigation is app-specific. To see what a user has access to, you need to first understand each application’s privilege and access model.
- Check if there are stale admin or user accounts that haven’t been accessed recently and can be reclaimed.
- Examine security configurations to make sure that everything looks good and there has been no drift.
Even by following these steps, admins can miss threats that are only visible when they look at privileges and activity across applications. Does a user have a toxic cocktail of privileges across multiple SaaS apps? Has a user downloaded a large number of files from G Drive and reports from Salesforce?
A lean security team tasked with defending SaaS applications that may be managed by application admins with limited (or no) security expertise can be overwhelmed by the demands of SaaS security. So what is the beleaguered security team to do to protect SaaS efficiently? The key to efficiency is automation and the use of purpose-built tools that protect the time of scarcest resources.
Automating Cloud Security Operations
Security must find ways to eliminate manual work wherever it’s possible, and augment manual effort with automation elsewhere. Cloud detection and response (CDR) capabilities can help organizations automate the most labor-intensive and time-consuming areas of SaaS security. Let’s look at a few of these areas:
Visibility
The first step in achieving comprehensive security is having continuous visibility of access, privilege, and activity. Security teams need:
- An inventory of users and access
- Role mapping
- Activity monitoring
- Authorizations to third party applications
CDR provides consolidated and centralized visibility and data-driven analytics to detect, investigate, and mitigate threats in the cloud. CDR solutions automatically aggregate data about users, privileges, activity, and configurations through API integrations. The data is normalized and enriched with context about users, devices, and locations. Rather than needing to manually poll applications for the data they need, security operations and IR teams can look at the data that has been pulled for them in one place.
Detection
Even with access to high quality data, security teams often have limited bandwidth to hunt for threats. CDR solutions offer out-of-the-box alerts based on detecting unmitigated risks, data breaches, account compromise, and insider threats. CDRs analyze privileges and activity within and across applications and apply machine learning and user behavior analytics to flag signs of trouble. For example,
- Is an account showing signs of compromise?
- Is a legitimate user acting in a suspicious or dangerous way?
- Are API being abused?
- Is there an unusually high number of login attempts from an unfamiliar location?
By ranking alerts according to impact, CDR gives lean teams a prioritized list of things to focus on. By providing rich consolidated activity data and all the analytics required to investigate potential issues in a single dashboard, CDR makes the lives of analysts, threat hunters, and incident responders on the team easier.
Response
When it comes to incident response and recovery, speed of data retrieval and analytics is key. Having ready access to data about users, privileges, and activity that IR teams need to analyze the situation makes a big difference in the outcome and impact. CDR gives investigators the data they need in a timely manner.
CDR solutions can also be configured to take remedial action for issues that require immediate attention. For example, security admins can tell the system to automatically lock compromised accounts, unshare files, and/or remove malicious mail forwarding rules and then send a notification to investigate further.
For organizations that use security orchestration, automation and response (SOAR) or IT service management to handle remediation, CDR tools provide downstream integration with these external tools.
Hardening
Posture management and security hardening is critical for reducing the attack surface and effectively blocking threats in SaaS applications. With the right kind of visibility, security teams can ensure that SaaS applications are configured according to best practices, detect and fix configuration drift, and remove stale accounts.
Conclusion
SaaS environments are inherently multi-cloud. The heterogeneity of identity and access, security controls, service maturity, and API access across SaaS apps makes the work of securing these applications particularly onerous. With some planning and preparation and using tools that are designed specifically for SaaS security such as Cloud Detection and Response, teams can improve their efficiency of SaaS security operations significantly. CDRs help to automate time-consuming repetitive tasks for visibility, monitoring, detection, response and security hardening, and allow threat hunters, SOC analysts, and IR teams to focus on security.
Interested in learning more? Read our whitepaper for actionable insights and strategies.