Consolidate visibility for your entire SaaS security posture.

Measure how any posture change will affect your users before you make it.

Promote continuous compliance of SaaS applications with regulatory standards.

Limit data exposure via poor hygiene and broad access.
Take action to secure your SaaS configurations.
Discover and address vulnerabilities across your SaaS applications. Obsidian helps you implement proactive measures to limit the likelihood and blast radius of a security incident before it’s too late.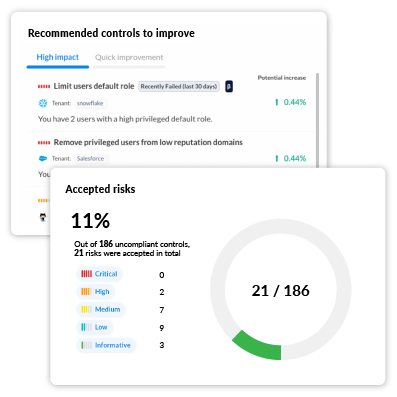
Improve controls with recommendations informed by Obsidian expertise and benchmarks established by organizations like CIS.
Measure the strength of your security posture with a comprehensive posture score and comparisons against other Obsidian environments.
Prevent configuration drift and understand the evolution of your SaaS security performance over time with posture history.
Initiate security review and remediation directly from Obsidian using bi-directional integrations with services like Jira and ServiceNow.
Make SaaS compliance a continuous commitment.
Get a real-time view of how your SaaS applications fare against relevant standards. With Obsidian, you’ll achieve and maintain continuous compliance so your business can focus on building trust and unlocking new sales opportunities.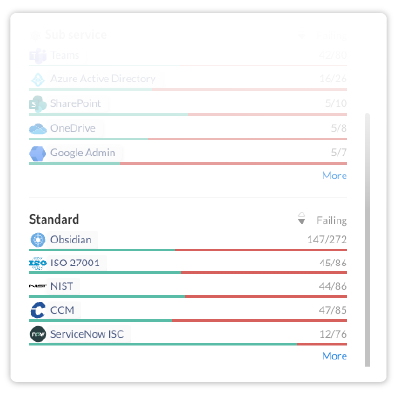
Monitor compliance in real-time against internal security standards and regulatory frameworks like NIST 800-53, SOC 2, and CCM.
Identify and promptly remediate failing security controls putting your organization at risk of noncompliance.
Communicate compliance to stakeholders and auditors with comprehensive, automatically generated reports
Rope in user privileges and sensitive data access.
Limit the delegation of SaaS privileges and data access to the users who actually rely on it. Obsidian gives you the context needed to minimize risk without worrying about causing any surprise disruptions to business operations.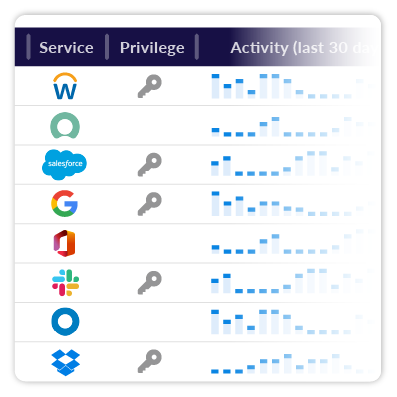
Leverage activity data to determine when users are entrusted with privileges they aren’t using and make appropriate adjustments.
Use title and peer group analysis to identify users whose privileges are unusually generous and unnecessarily risky for their roles.
Investigate sudden privilege escalations to ensure they’re necessary and not indicative of malicious activity.
Understand access to potentially sensitive resources and areas where business data is shared publicly.