
Monthly SaaS breaches have increased 300% year-over-year, highlighting the urgent need for SaaS security.
One observed SaaS attack lasted just 9 minutes from initial access to sensitive data exfiltration—security solutions need to be quicker.
84% of compromised accounts have MFA enabled, showing that protections like MFA are not enough.

- Kickstart with out-of-the-box detection rules mapped to the MITRE ATT&CK framework
- Leverage ML-based detection rules informed by hundreds of incident response engagements to identify threats
- Customize detection rules with automated backtesting to adapt to your specific environments
- Start with tailored remediation steps to accelerate response efficiency
- Easily search human-readable SaaS logs to quickly pivot on IP, user, geolocation, and event type for efficient triage
- Integrate with SIEM and SOAR platforms to automate incident response workflows

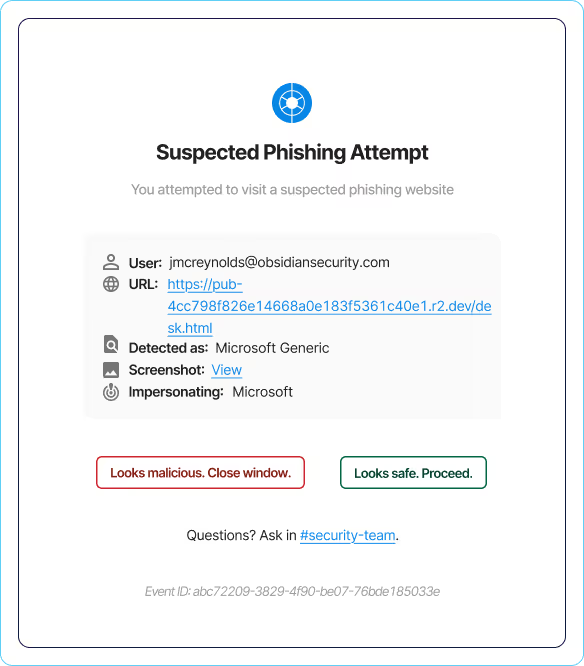
- Prevent users from submitting credentials to phishing sites
- Stop 100% of spear phishing attacks from popular Adversary-in-The-Middle (AiTM) kits
- Gain context into phishing attempts to identify high-risk users and applications
- Gain a normalized view of non-human identities to detect suspicious behavior across apps within Google, O365, and Okta
- AI-powered models detect anomalous events like if new data or resources are accessed, or different infrastructure is used
- Get alerted when non-human identities are leveraged in an atypical manner, indicating compromise

Defend against AiTM attacks in minutes to secure your SaaS identities.
Detect, respond and prevent phishing attacks before they compromise your SaaS.
Detect and respond to attacks like social engineering before data exfiltration.
Start in minutes and secure your critical SaaS applications with continuous monitoring and data-driven insights.