And attackers move laterally in minutes.
Get accelerated SaaS threat detection and prevention.


- Stop attack vectors like SSPR, SIM swapping, and helpdesk social engineering before data loss
- Identify anomalous user behaviors using ML-based algorithms
- Leverage out-of-the-box detection rules, informed by incident response engagements and mapped to the MITRE ATT&CK framework
- Customize rules to adapt to your specific environment
- Receive actionable alerts with details like role, privilege level, locations, and behavior to respond quickly to SaaS threats
- Baseline user behavior trends to expedite alert triage
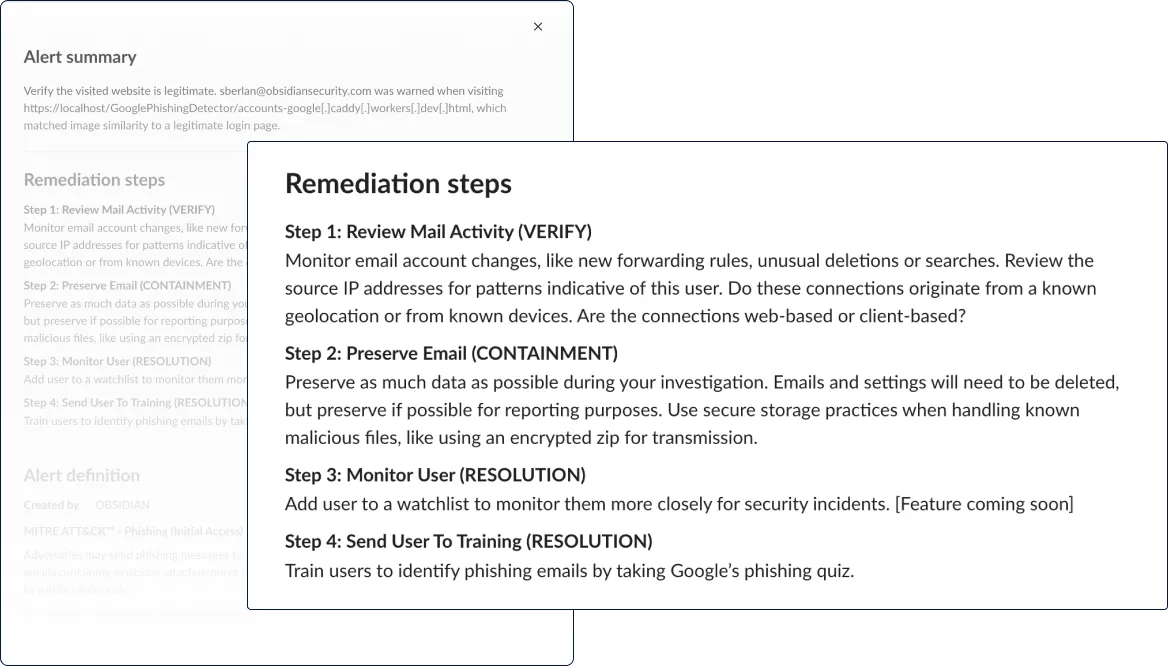
- Start with tailored remediation steps to accelerate response efficiency
- Drive investigation and hunt for additional insights with searchable SaaS logs
- Integrate with SIEM and SOAR platforms to automate incident response workflows

- Improve your threat detection with growing insights from hundreds of IR engagements and deployments
- Gain insights into high-risk users and applications across your SaaS environment
Start in minutes and secure your critical SaaS applications with continuous monitoring and data-driven insights.