Social engineering attacks have evolved significantly, and one of the most concerning trends is the targeting of help desk agents. These attacks exploit human vulnerability, bypassing technical safeguards to gain unauthorized access to systems. The well-documented MGM attack is an example of help desk social engineering [1]. This attack continues to grow in the wild based on successes seen by the attacker community. In fact, the U.S. Department of Health and Human Services (HHS) issued an alert [2] on this topic warning healthcare organizations of a spike in threat actor activity.
This blog post explores insights from recent attacks we’ve observed using help desk social engineering as the infiltration tactic, and identifies steps organizations can take to defend themselves against these attacks.
Insights from the HHS Sector Alert
The HHS Sector Alert issued by the Health Sector Cybersecurity Coordination Center in April 2024, emphasizes the growing threat of social engineering attacks targeting help desk personnel. According to the alert, these attacks often involve sophisticated pretexting. Attackers impersonate legitimate users or trusted entities to extract sensitive information. The memo underscores the need for increased vigilance and training among help desk staff to recognize and thwart these deceptive tactics.
AI Voice Cloning Attacks
With the rise of AI tool availability, cybercriminals increasingly turned to AI voice cloning technology to execute sophisticated social engineering attacks. By using AI to clone the voices of senior executives, attackers convincingly impersonated them in phone calls to help desk agents and other employees. This new breed of scam leverages artificial intelligence to exploit trust and authority, making it harder for victims to recognize the deception. These attacks highlight the growing intersection of AI and social engineering, presenting new challenges for security professionals [3].
Understanding Help Desk Social Engineering With Real World Examples
Obsidian’s research team continuously monitors user behavior and system access to identify anomalies that may indicate a help desk social engineering attack. This is further informed by incident response engagements as well as incidents observed within customer deployments. These attacks also include other tactics such as adversary in the middle and self service password reset abuse, to facilitate the compromise across the SaaS kill chain.
We recently observed and stopped two such attacks. Documented below are tactics used by the attackers indicating their sophistication as well as informing the defense strategy organizations need to employ against this threat.
Attack 1: Chief of Global Operations at Medical Technology Company
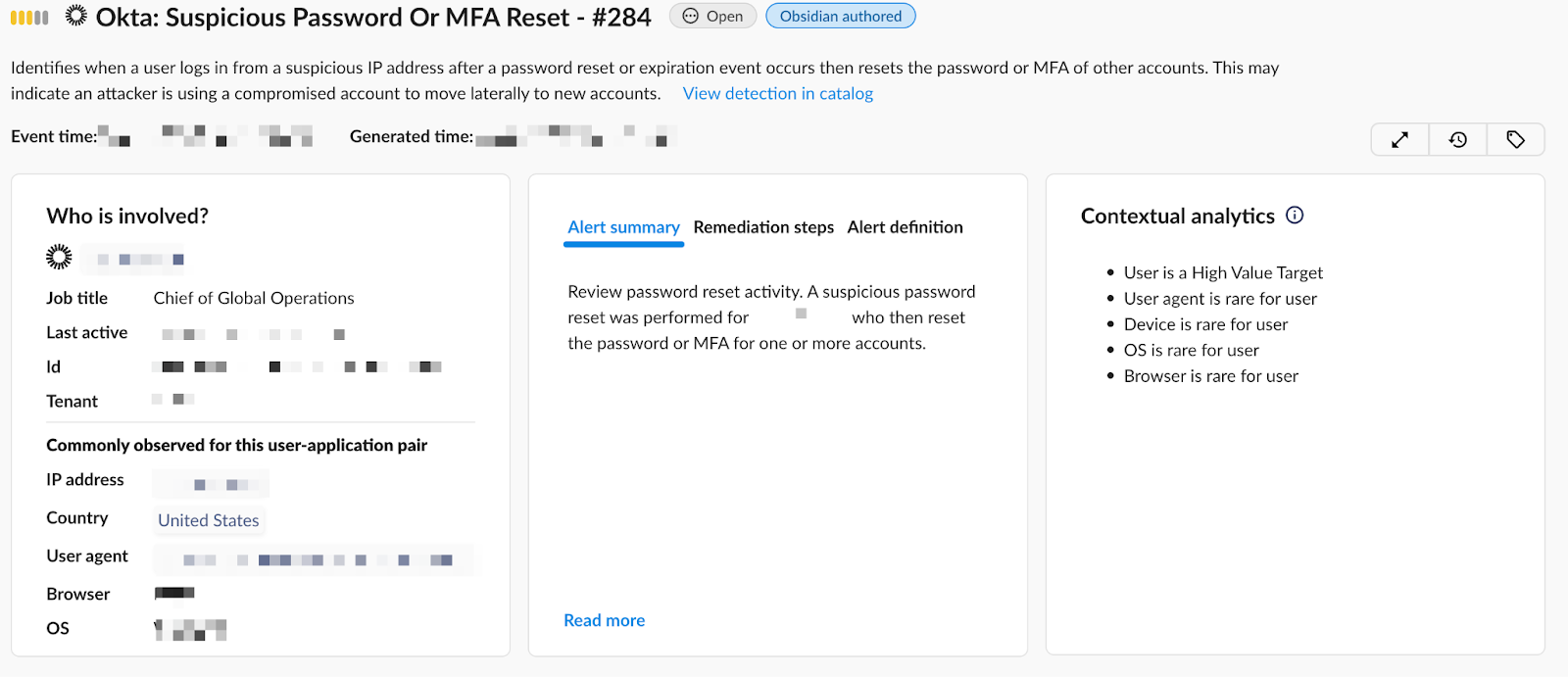
In this example, the threat actor targeted the Chief of Global Operations of a medical technology company. At the outset, it’s clear that the attacker targeted a high-profile user—someone with access to data.
The attacker contacted the help desk on behalf of the user to reset the user’s password. In addition, the attacker also reset the MFA device associated with the account. These are two steps we often see in most help desk attacks. However, MFA offers a strong layer of defense, and most users believe they are protected with MFA. Yet,attackers have figured out ways to subvert MFA. Over the last 12 months, we’ve seen attackers subverting MFA in 70% of SaaS breaches.
As highlighted by the alert below, a combination of these events is highly suspicious—often malicious. A high-value user had their password reset, MFA device reset, and activity generated from a device type that is not typically seen for this user.
The attacker sought to access a set of documents to research the company infrastructure and seek information that would enable them to move laterally (fortunately, they were stopped before this could happen!). These included documents named similar to the following:
- IT First Day Onboarding
- VPN Enrollment Guide
- AWS Configuration
Your spidey senses better go off when you see something like this!
Attack 2: Insurance Specialist at Healthcare Facility
In this next example, the threat actor targeted an Insurance Specialist at a healthcare facility. This incident presents many interesting insights.
The targeted user again had access to healthcare data on the facility’s customers. Password reset was again the goal—in this case, it originated from an on-premise AD server—as was the MFA update (the Duo phone number).
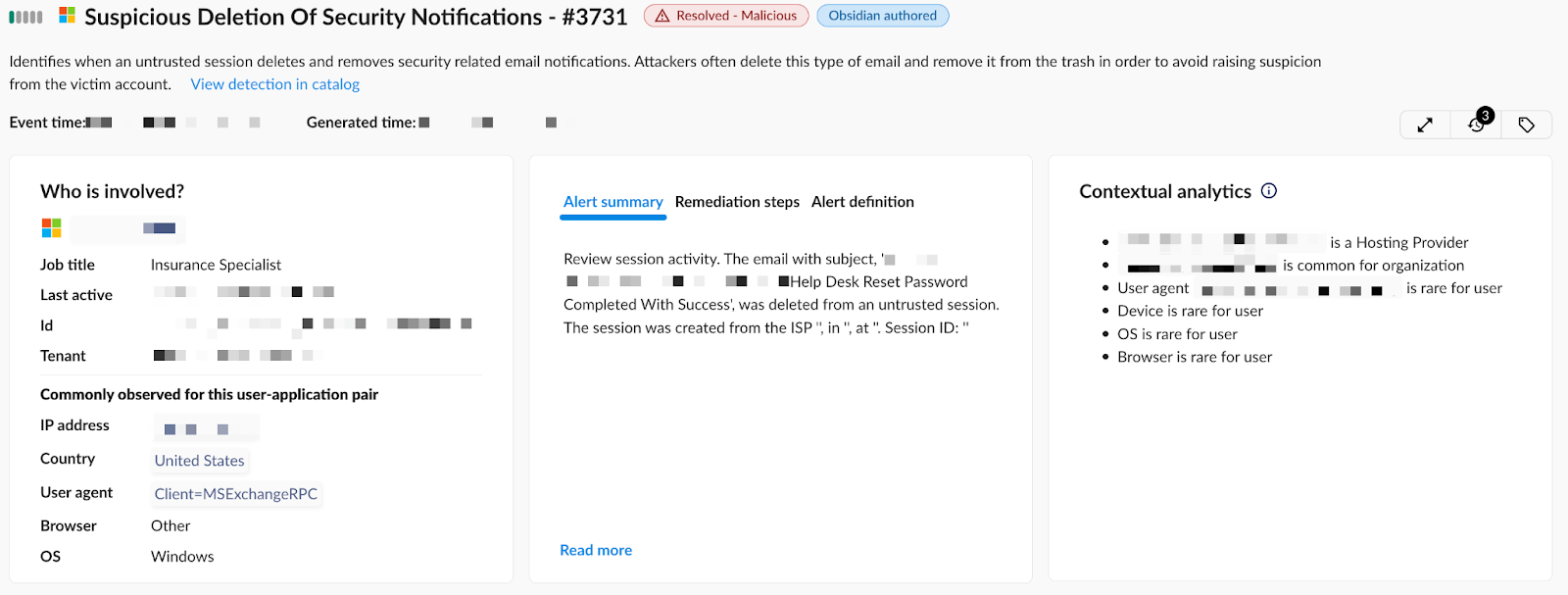
What was interesting in this case was the next step—the attacker logged into the victim’s mailbox using the new Duo phone number as MFA and deleted the email notification for the help desk password reset. This is another pattern we observe with password and MFA resets.
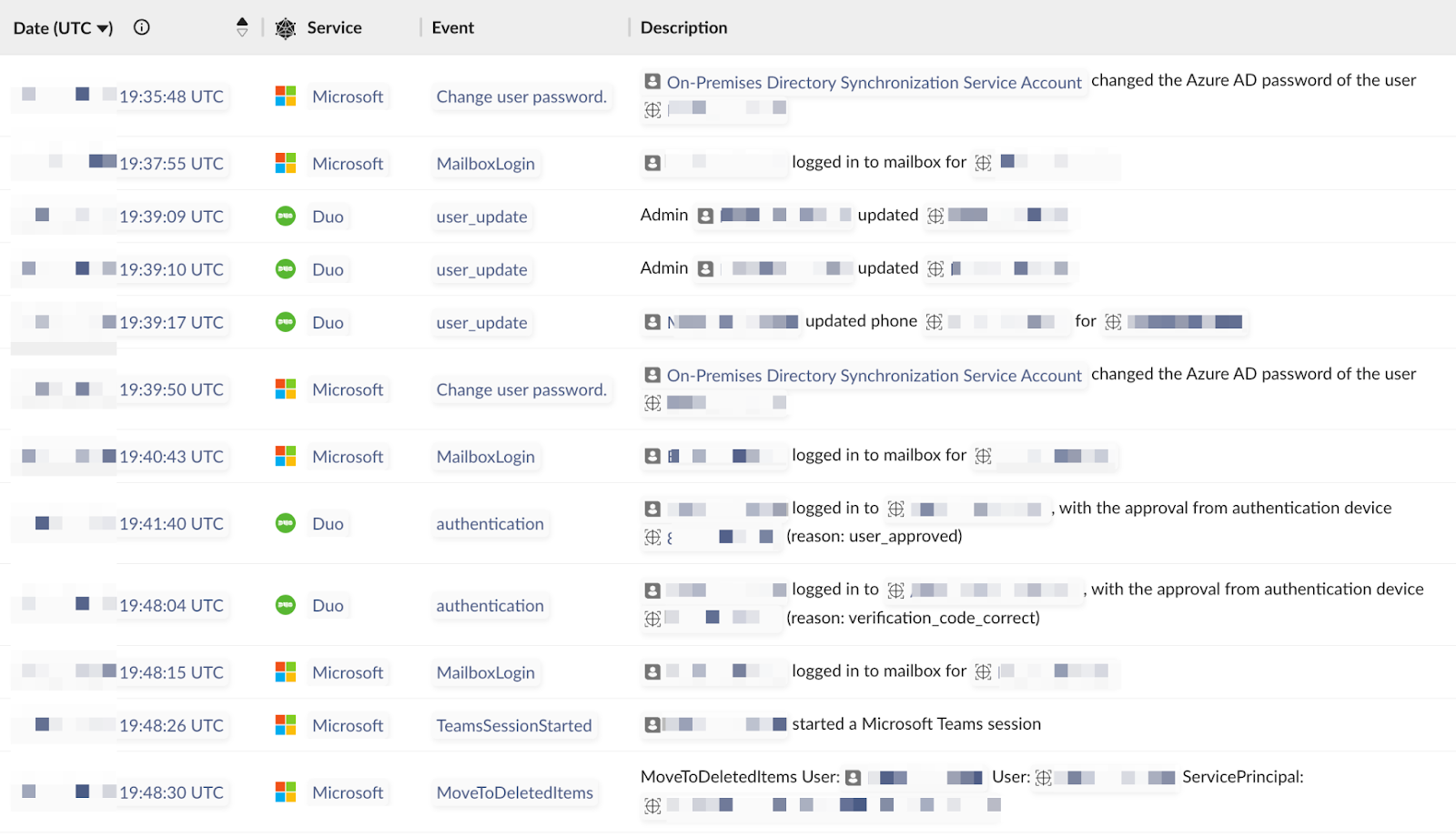
These activities present multiple opportunities to detect them, as seen below—deletion of the password reset email or changing the MFA to a different phone number. Nevertheless, both activities are common by themselves. It’s, the context that is indicative of a problem.
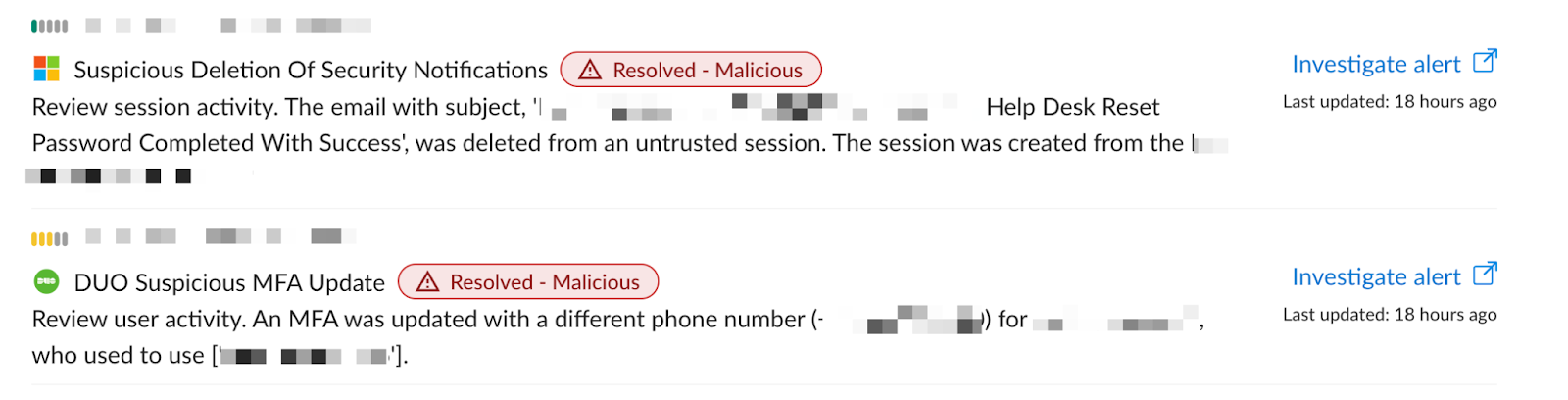
The first alert triggered for the suspicious MFA update for the victim’s registered Duo phone number originated from a hosting provider such as Digital Ocean or bulletproof hosting providers typically used by threat actors. Interestingly, the threat actor also chose an IP location that was common for the organization, suggesting this was a planned and well-researched attack. We have observed threat actors using residential proxies and VPN providers to get IP locations close to the organization’s locations to subvert geofencing and country blocklists.
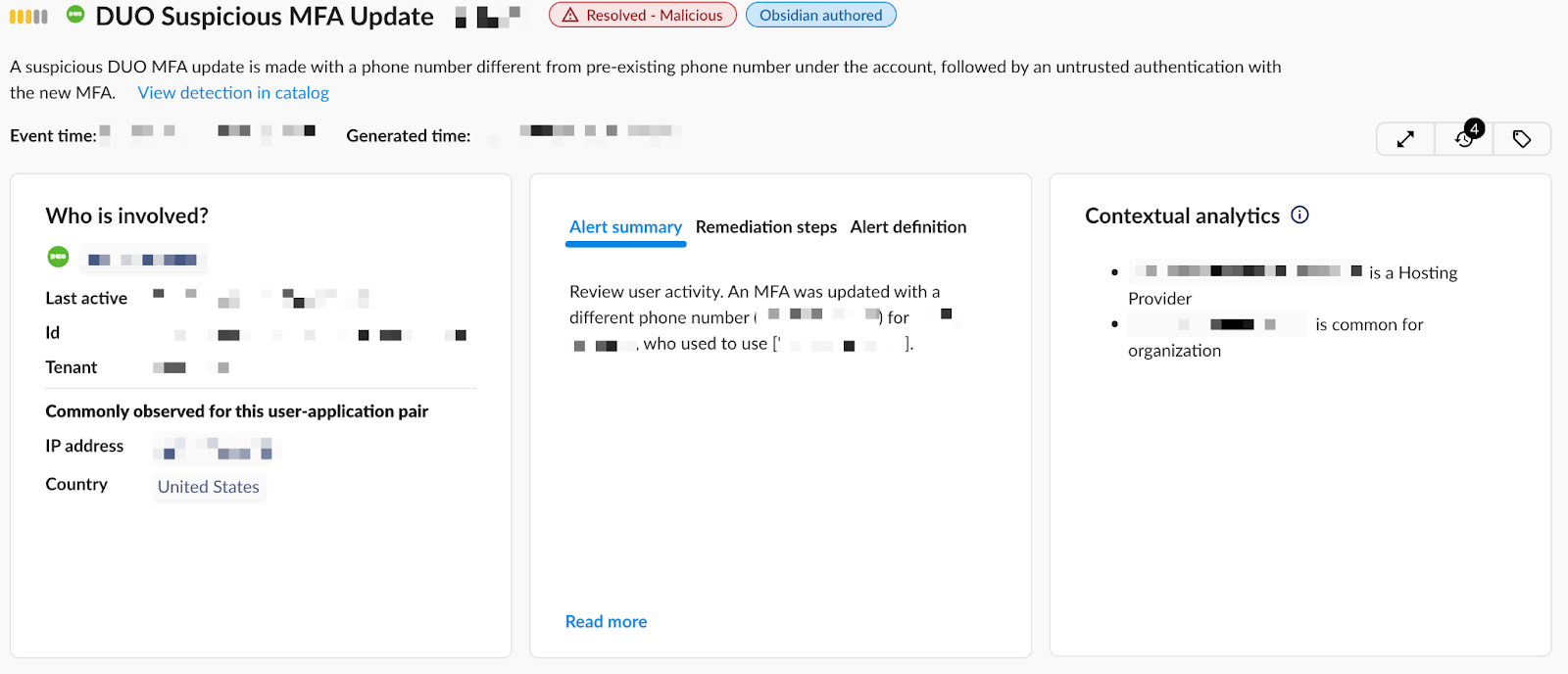
The next alert concerns the deletion of the security notification from the victim’s inbox. In this case, the important context is the device from which the deletion operation was executed. We see that this activity was performed from a device with rare elements such as the operating system and browser.
Steps to Safeguard Against Help Desk Social Engineering
The aforementioned tactics highlight the challenges organizations face when trying to stop attackers. However, it is possible to take several security measures to minimize the risk of help desk social engineering.
1. Perform Regular Training and Simulations:
Help desk agents should undergo regular training to identify and respond to social engineering attempts. Simulated phishing exercises can help staff stay sharp and recognize red flags in real scenarios.
2. Implement Identity Verification Procedures:
Stringent verification processes for help desk interactions can prevent unauthorized access. These may include multi-factor authentication and cross-verifying requests through multiple channels.
3. Encourage Incident Reporting:
Encouraging staff to report suspicious interactions promptly can help organizations respond swiftly to potential breaches and analyze patterns to strengthen defenses.
4. Monitor and Alert to Suspicious Credential Usage and Modifications:
Monitoring and alerting for suspicious activities, such as MFA deactivations and password resets, is crucial. Ensure your SaaS security platform can detect unusual patterns or behaviors related to these actions, triggering alerts with relevant context for security teams to investigate and respond promptly. This proactive approach helps to mitigate risks before they can be exploited by attackers.
5. Limit Impact with Secured Configurations of your SaaS Applications:
As was clear in both attacks, threat actors target users with access privileges. Ensuring that your SaaS applications are configured securely can limit the impact of any potential breach. This includes enforcing the principle of least privilege, ensuring access controls are properly configured, and regularly reviewing permissions to prevent unauthorized access. Your SaaS security platform can automate this workflow. This is especially crucial when you have tens or hundreds of SaaS applications to defend. It can help manage configuration drift, reduce over privileges, provide continuous monitoring and automated alerts to identify and remediate misconfigurations before they can be exploited.
Conclusion
The evolving landscape of cyber threats necessitates a proactive and layered defense strategy. As demonstrated by recent attacks and the emergence of AI voice cloning scams, social engineering can have devastating impacts.
Obsidian Security helps organizations comprehensively detect, prevent, and respond to help desk social engineering threats and many other SaaS threats. For more detailed information on how Obsidian Security can help protect your organization, contact us or explore the various use cases at www.obsidiansecurity.com.
References
[1] SOCRadar Cyber Intelligence Blog on MGM Casino Hack
[2] HHS Sector Alert on Help Desk Social Engineering
[3] McAfee Blog on AI Voice Cloning Scams




