It’s Obsidian’s inaugural SSPM Week, and over these last few days we’ve announced a number of exciting releases and additions to our platform. Managing SaaS integration risk, measuring and maintaining SaaS compliance, extending security across niche and custom applications—we’ve covered a lot of ground in a short time.
Still, we recognize that every organization is at a unique point in their SaaS security journey and that a number of teams are still trying to better understand its challenges. Education and conversation is important, which is why we’re so excited to share the latest additions to our Obsidian Lightboard Learning Video Series.
Our new batch of lightboard videos covers five important and relevant SaaS security topics:
- SaaS incident response
- Continuous SaaS compliance
- The three pillars of SaaS security
- Third-party SaaS integration risk
- Techniques of SaaS compromise
Below, we’ll share a little bit of what you can expect from each lightboard video and explain why these topics are so directly relevant to your organization’s security.
SaaS Incident Response
As sensitive data workflows migrate to SaaS, the volume of attacks targeting these services will only continue to grow. A thorough SaaS incident response strategy is critical for identifying, investigating, and resolving these threats in an effective and complete manner.

In this lightboard video, our co-founder and CTO Ben Johnson walks through the four distinct phases of the NIST incident response lifecycle: preparation; detection and analysis; containment, eradication, and recovery; and post-event activity. His guidance for each step is informed by experience in countless SaaS incident response engagements. Everything Ben shares, he ultimately ties back to a fundamental goal: how can I speed up my detection and response efforts while also slowing attackers down? Check out the full video here.
Achieve Continuous SaaS Compliance
Organizations that rely on SaaS must consider their applications as part of their broader regulatory compliance requirements. When your financial records, customer and employee information, proprietary code, and countless other forms of sensitive data reside within these services, noncompliance puts your business and its reputation at serious risk.
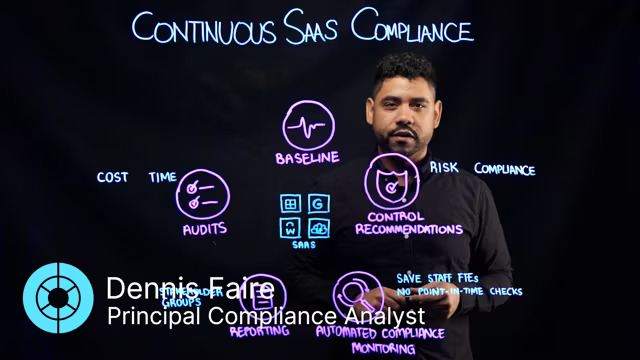
In this lightboard video, Obsidian Principal Compliance Analyst Dennis Faire provides a new way of thinking about SaaS compliance as a continuous process. Manual audit preparation is difficult with dozens of applications, thousands of settings, and extensive required expertise. By automating the process of mapping SaaS controls to compliance standards and monitoring their status in real-time, you can ensure adherence with any standards while cutting time and costs. Learn more about continuous SaaS compliance in the lightboard.
The Three Pillars of SaaS Security
The conversation around SaaS security often focuses on users and how they’re interacting with an application—but the reality of modern SaaS environments is a lot more complex. SaaS integrations are increasingly connected with one another and with a wealth of third-party and custom integrations. Each application is complex with its own unique roles, permission models, and configuration options.

In this lightboard video, Obsidian co-founder and CPO Glenn Chisholm shares a new way of thinking about SaaS security which focuses on three main pillars: SaaS posture, integration risks, and threats. Posture is an analysis of your SaaS applications and their security settings, controls, permissions, and overall risk surface. Integration risk focuses on the discovery of what applications are connected, what permissions they hold, where data flows, and what risks this introduces. Threat details the ways that attackers can exploit user and integration connections to gain persistent access to the SaaS environment and data within it. Learn more about the three pillars of SaaS security in the video.
Third-Party SaaS Integration Risk
SaaS applications are designed to be interconnected, creating a seamless user experience with data synchronization between platforms, third-party integration, and custom developed tools. At the same time, this interconnectivity makes it difficult to understand where your data resides and what security vulnerabilities exist in your environment.
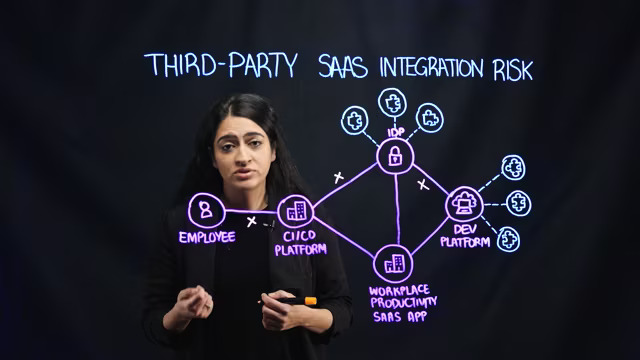
In this lightboard video, our Head of Product Neha Duggal explores the risks that third-party SaaS integrations can create not only for one organization’s security, but also for other businesses connected to it. She illustrates this with an example of an actual breach at a continuous integration and continuous delivery vendor that ultimately affected a customer’s GitHub environments and other companies involved with the platform. Learn more about third-party risk and hear the full story here.
Techniques of SaaS Compromise
Authentication measures have evolved beyond simple credentials with the use of identity providers and measures like single sign-on and multi-factor authentication. In response, attackers have increasingly foregone credential-based attacks in favor of new techniques designed to compromise a user or SaaS integration.
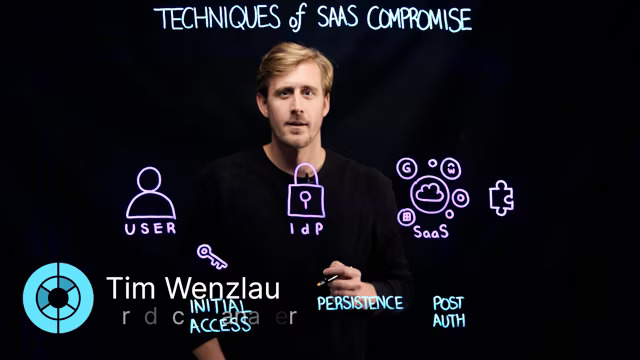
In this lightboard video, our Principal Product Manager Tim Wenzlau shares some insights around the techniques attackers are more frequently using to compromise SaaS environments, along with the measures they often take to ensure their access is persistent and long-lived. Adversarial techniques like SaaS session hijacking and MFA fatigue attacks can help bad actors entirely bypass additional security measures—or, they can entirely forego users and target a SaaS integration instead. Once in, attackers can escalate privileges, create new user accounts, and define new rules to make their access discrete and persistent. Learn more about techniques of SaaS compromise in this lightboard.
Discover Our Entire Lightboard Series
The five lightboard videos in this blog span only a few of the exciting and important topics in SaaS security that our team is contending with on a daily basis. We’ve discussed other concepts like zero trust for SaaS and SaaS session hijacking in some of our other videos; to see them all in one place, check out our Lightboard Learning Series page!