On 12 January 2024, Microsoft disclosed a critical breach carried out by Russian state-sponsored group, Midnight Blizzard. The threat actor used a password-spraying attack to gain unauthorized access to Microsoft Corporation’s Office 365 tenant–affecting the accounts of senior leaders and members of Microsoft’s cybersecurity and legal teams.
Who is Midnight Blizzard?
Midnight Blizzard, also known as Nobelium, APT29, and Cozy Bear, is a well-known threat actor. The group was responsible for the SolarWinds Hack, one of the most significant cybersecurity attacks in history. In that attack, malicious code was inserted into SolarWinds’ Orion software–affecting thousands of organizations (including the US government) and causing billions of dollars in damages.
While the Microsoft breach had a relatively limited impact, the threat actor managed to evade detection for months, reflecting their persistent and stealthy nature. Now, let’s explore the attack timeline in further detail…
Microsoft breach timeline:
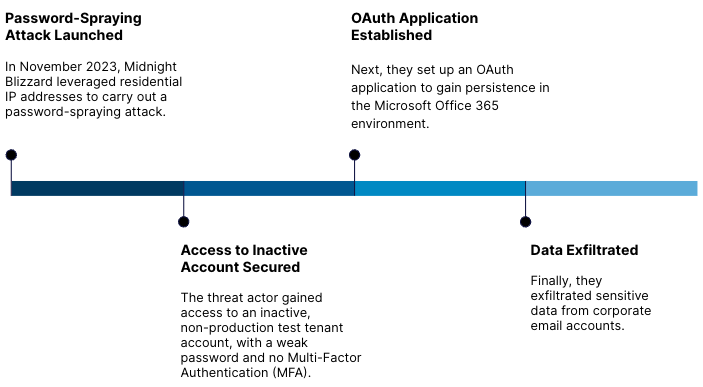
Why it Matters
This incident reflects the ongoing threat posed by nation-state actors and the need for proactive measures to secure SaaS applications as they become even more vulnerable to attacks.
Midnight Blizzard’s more recent breach of Hewlett Packard Enterprise (HPE) is yet another example of this. The breach, which began in May 2023, went undetected for several months. During this time, the threat actor gained unauthorized access to HPE’s cloud-based email environment leading to the exfiltration of corporate data.
What Can You Do to Protect Your Organization?
Below, we offer guidance to help you secure your SaaS applications against attacks like the Microsoft breach. We outline measures to reduce the risk of breaches (prevention) and detect and stop threats early in the kill chain (mitigation).
At a Glance
Prevent SaaS compromise by:
- Enforcing mandatory reviews for privileged accounts
- Identifying and removing inactive accounts
- Leveraging controls that block unauthorized integrations
Mitigate threats by:
- Detecting and removing high-risk applications
- Identifying and swiftly addressing user compromise
Let’s now explore each of these measures in further detail…
1. Enforce mandatory reviews for privileged accounts
User access reviews are crucial for security and IT teams to enforce the principle of least privilege. This helps minimize data exposure to only what is necessary. In the case of a breach, restricting data access limits the impact of the threat, preventing it from causing further damage to the organization.
Obsidian offers tools to help you do this effectively. Our platform allows you to:
- Identify all accounts with special privileges.
- Track the creation and usage of user and service accounts.
- Verify whether Multi-Factor Authentication (MFA) is being applied at every login.
- Initiate reviews for newly assigned accounts.
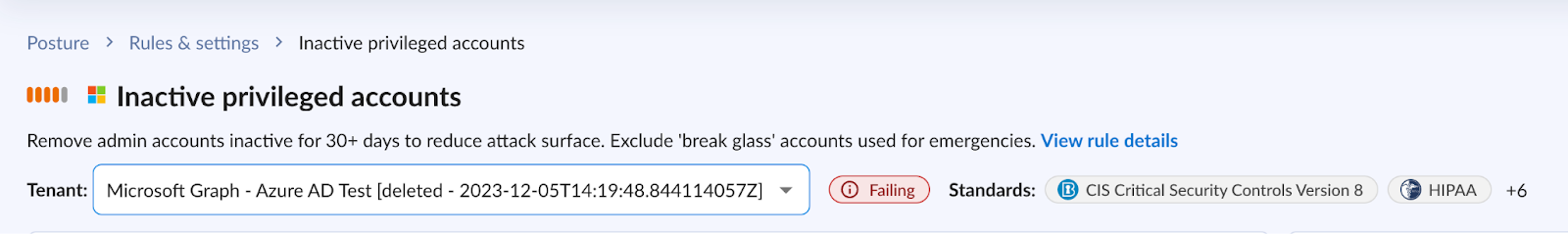
2. Identify and remove inactive privileged accounts
As illustrated in the Microsoft breach, inactive accounts can pose a significant security risk. These accounts serve as an ideal entry point for threat actors to gain unauthorized access, as they often go unmaintained and unnoticed by security teams.
You can use Obsidian to help you efficiently detect these accounts, particularly those with special privileges. Inactive account alerts like the one below, play a crucial role in helping you identify, tune, or deprecate accounts, resulting in a reduced attack surface for threat actors.
3. Leverage controls that block unauthorized integrations
The rise of interconnected SaaS applications poses new challenges for organizations. As integrations become more seamless, the risk of unauthorized or insecure third-party applications increases.
Using Obsidian’s controls, you can block unauthorized applications from accessing your environment (as shown below). Obsidian also provides filters that offer immediately actionable data, surface risky permissions, user activity levels, and specific detections related to suspicious integration activities.
4. Identify and remove high-risk applications
Applications are typically classified as “high risk” if they access sensitive data, have weak authentication, or exhibit other qualities that increase their vulnerability.
Obsidian’s Integration Risk Management (IRM) capabilities help you:
- Identify high-risk applications
- Gain critical context into the application (e.g. what data it has access to)
- Streamline the review process
- Automate the removal of risky applications
As shown below, our platform promptly identifies high-risk applications. In this instance, it flags those applications that can read all mailbox content, as experienced in the Microsoft breach.
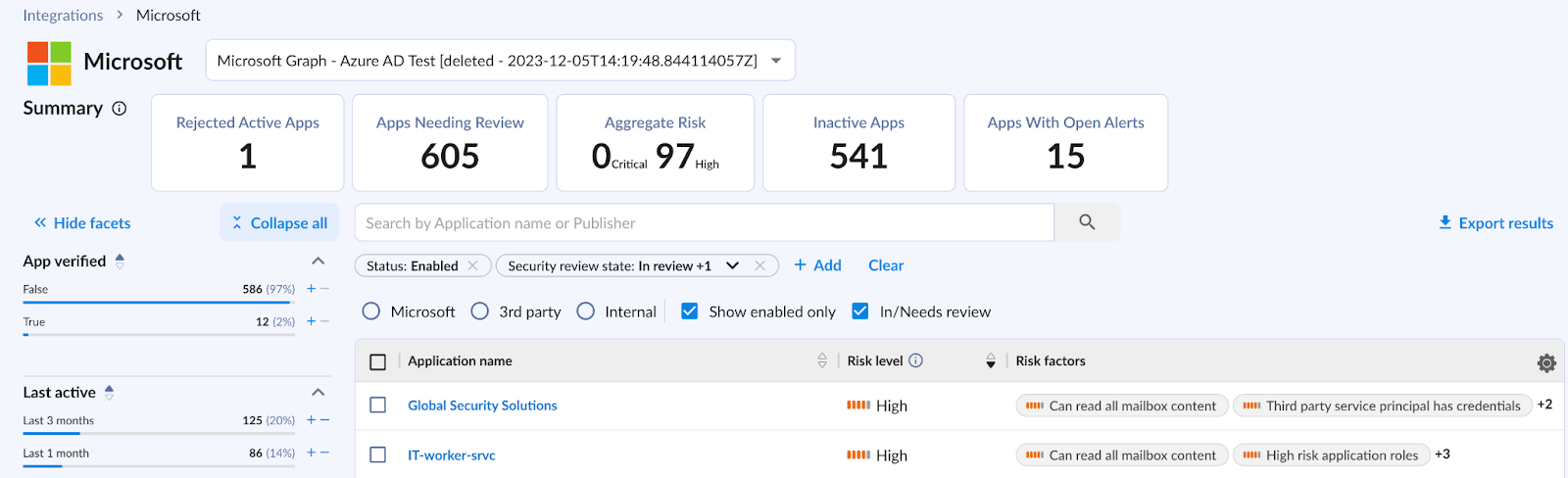
As demonstrated below, you can configure triggers that automate the removal of high-risk applications, tailored to the needs and risk tolerance level of your organization.
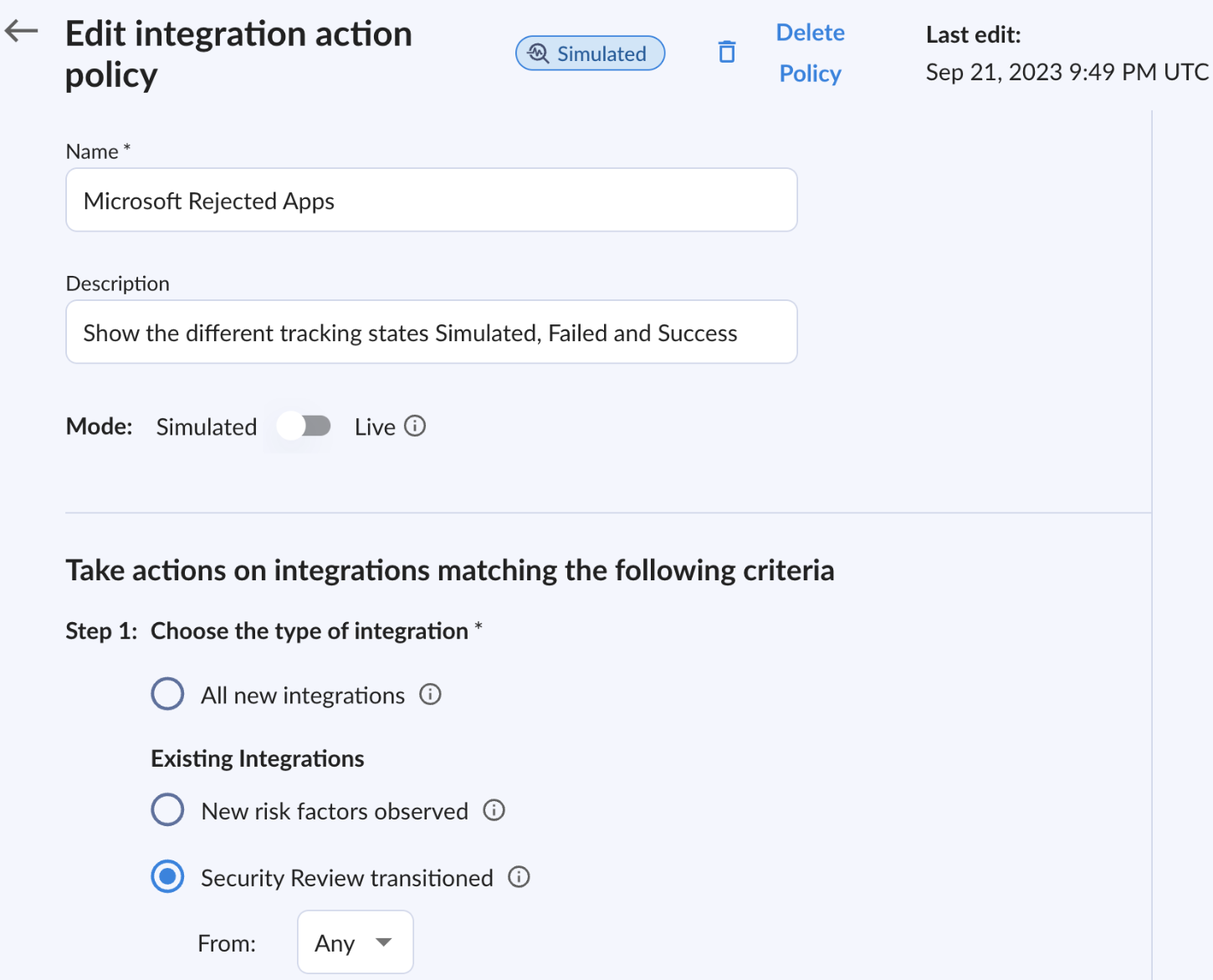
If the application was not removed by the team during review, an extra layer of detection can be added, which would classify the application as a threat:
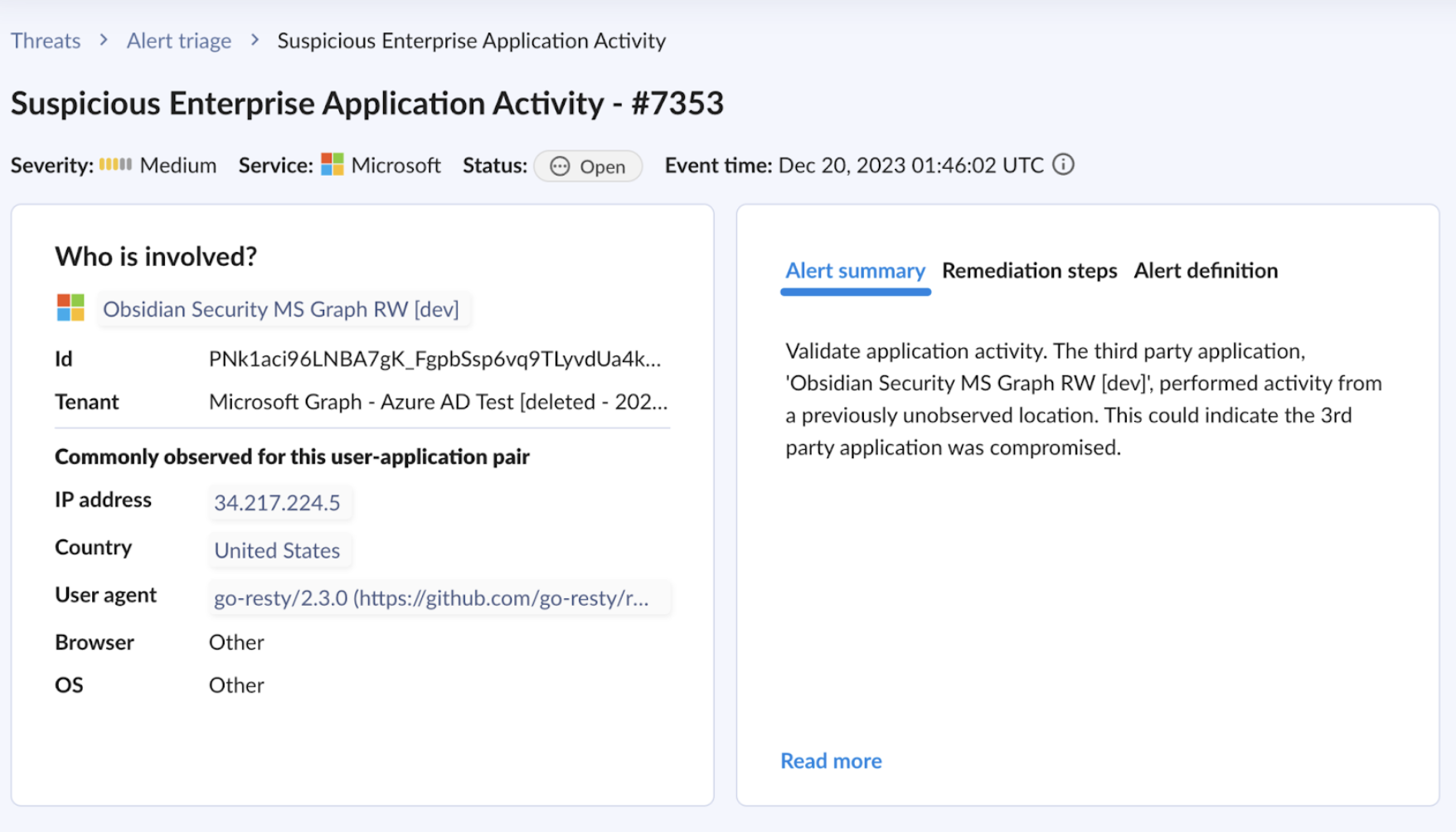
5. Identify and swiftly address user compromise
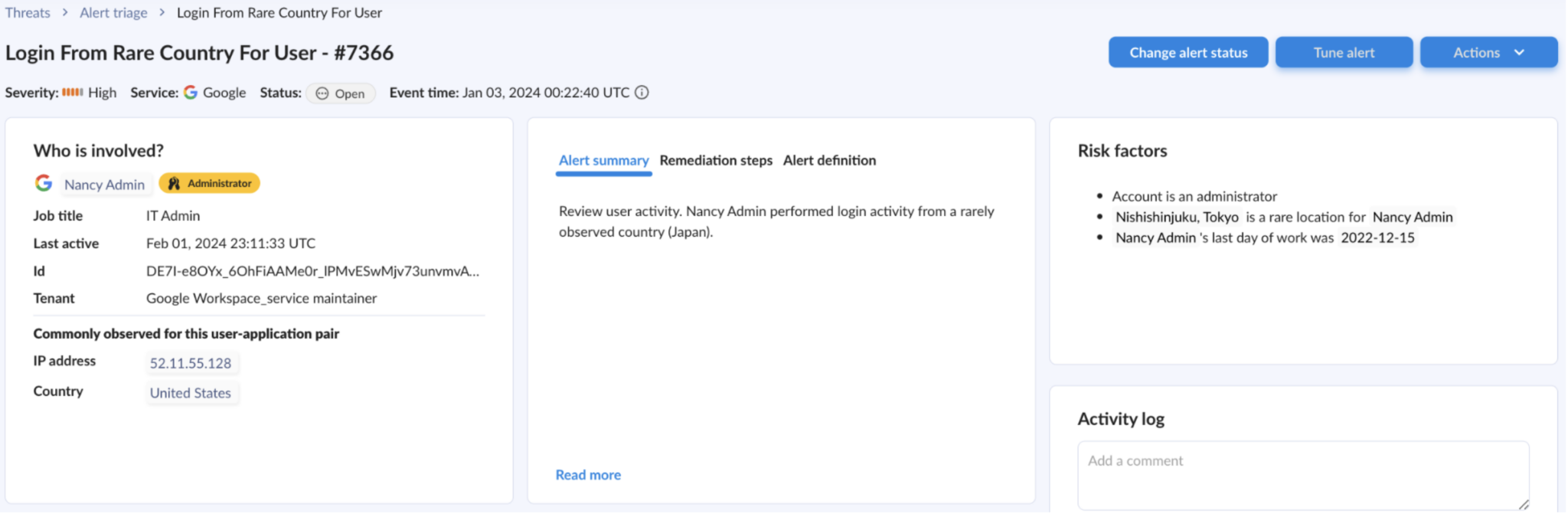
Addressing user compromise in a timely manner helps minimize additional fallout from a breach. Obsidian provides a range of tools to help you conduct Identity Threat Detection and Response (ITDR).
Obsidian collects data from your SaaS applications, analyzing activity, configurations, and user behavior to understand what normal looks like within your environment. In the event of anomalies, such as impossible travel, Obsidian ensures you receive immediate, accurate and low-noise alerts. These alerts come with actionable insights that seamlessly integrate with your existing workflows for efficient incident response.
Final Thoughts
The recent spate of attacks by Midnight Blizzard is undoubtedly concerning. SaaS applications are increasingly the lifeblood of many organizations. Securing these applications is critical to minimizing and managing business risk for all organizations. As this blog post highlights, there are a number of actions you can take to secure your SaaS applications today.
For more information on how Obsidian can help you, download The Forrester Wave™: SaaS Security Posture Management, Q4 2023, or schedule a demo today.




