In the first post of this series on data guardianship at Obsidian, I introduced our core principles, including a commitment to transparency. In this post, I’m going to dive into what we mean when we talk about privacy and why Obsidian adopted a “data guardianship” practice instead of a thin privacy policy.
America’s history with the concept of privacy is muddled and awkward, stemming from the lack of a constitutional right to privacy. Privacy as a legal right rests on a flotilla of court cases which are tortuously drawn from interpretations of the fourth amendment prohibiting unreasonable searches and seizures. When it comes to data privacy, the concept of searches and seizures is a poor framework because it does not protect data willingly shared or submitted nor does it protect data passively collected for “reasonable” purposes. At Obsidian, we are absolutely committed to complying with relevant legislation but we are also aware that laws may not encompass the full scope of data guardianship a reasonable customer should expect.
More recent legislation including the EU’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have begun to establish new types of rights related directly to understandings of privacy defined as the right not to give or share information to others. This is a better match with people’s lived experience of privacy – “the right to be let alone” (Warren and Brandeis, 1890). Still, being “let alone” is not as straightforward; privacy comes in degrees.
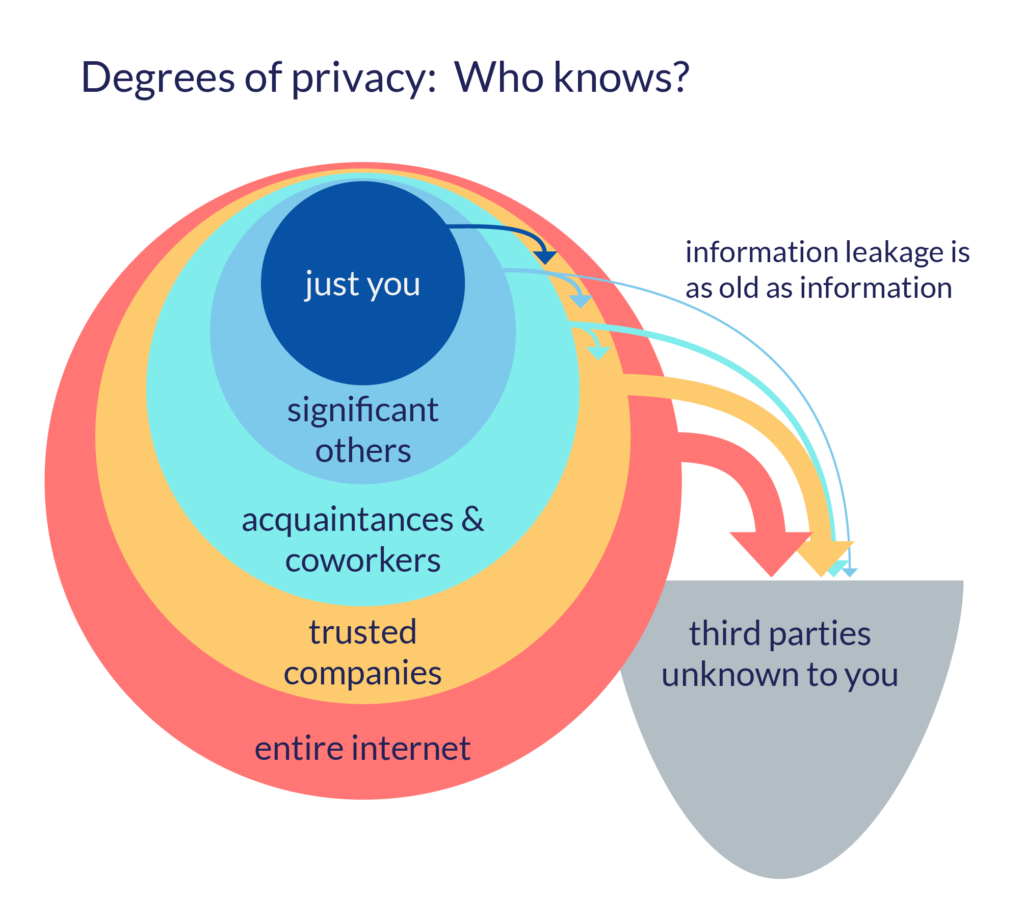
Degrees of privacy
Being let alone and allowed to keep to oneself could mean withholding information from literally everyone else so that only you have access to a piece of information. This is the strictest degree of privacy, but while it may be a strong privacy posture, it’s often not that useful. If, for instance, I alone know that there is a lump in my breast, I cannot benefit from having the lump diagnosed. In order to be empowered by information, in most cases, we must share it. What we usually talk about when we talk about privacy is information which has been shared with a limited set of trusted significant others such as spouses, parents, children, close friends, and trusted professionals like doctors, lawyers, or therapists, but nobody else. The degrees of privacy loosen further as information is shared with acquaintances and coworkers, trusted companies. Sharing with the entire internet or the broad public is the least private, but people who share broadly still retain some usage rights that can be enforced. The diagram is a bit too tidy – some information known only to the individual is also shared with trusted companies such as banks.
In corporate settings, what we talk about when we talk about enhancing data privacy is often about preventing data leakage beyond an individual’s knowledge or control. Many of the guarantees in the GDPR, CCPA, HIPAA, and related pieces of data protection laws intervene to reduce the likelihood that sensitive data from an individual will end up under the control of an untrustworthy entity. The lack of trust could stem from the fact that the individual does not know anything about these third parties – who they are, how the third party benefits from the data – or that the individual has no agency to prevent their data from being used by the third party. This is the crux of what we talk about when we talk about data privacy: power. Often the key problem is not that a particular piece of information is knowable to another, but that having that knowledge gives one party more power. That advantage is increased if the data subject has no agency to prevent their data from shaping their opportunities in the world.
At Obsidian, we included transparency and communication as a core principle of our data guardianship activity to reduce unwanted power imbalances. In fact, the fundamental value proposition of our product is to increase the power imbalance in our customers’ favor. We give our customers greater knowledge power than the threat actors trying to infiltrate, exploit, or attack their enterprises. By communicating clearly about why we need the data we use, how we prevent data leakage and data over-collection, we are earnestly dedicated to becoming a trusted company in our trusted data ecosystem. We have the highest commitment to ensuring that customer data remains securely within our data architecture and that we are partners in favorably increasing the balance of knowledge power to their advantage.


